Shift Repetitive Product Security Work To Custom Agents
The easiest and most flexible way
to stay on top of the risks you actually care about
Jit’s Custom Agents connect to your code, cloud, ticketing systems, and documentation to customize your visibility into the product security risks that matter to your business, while providing the context needed to take action.
“Please track every PR that contains security issues from the last week and update it every day. Open a fix PR to resolve the newly introduced security risks.”

Select or build Custom Agents that align product security visibility with your objectives
Save and revisit Custom Agents in your Agent Gallery to continuously track and monitor the specific product security risks you care about most.
Agent Gallery
Add new agents from our agent template gallery to automate your workflows with AI

I highlight the most critical issues in your environment, uncover risky correlations, and validate them. I help you focus on triage and remediation where it matters most.


I show a prioritized list of SCA vulnerabilities on direct dependencies.

I show a prioritized list of SCA vulnerabilities on direct dependencies.

I find the top application vulnerabilities that breach SLA.

I monitor the security issues that are owned by each development team.

I check for secrets exposures across all your branches.

I monitor for CI/CD misconfigurations that could enable supply chain threats.

I consolidate and prioritize the most critical cloud misconfigurations.

I automate environment-wide checks to surface drift without manual hunting
Offload the work needed to monitor, enrich, and act on security risks that matter to your business
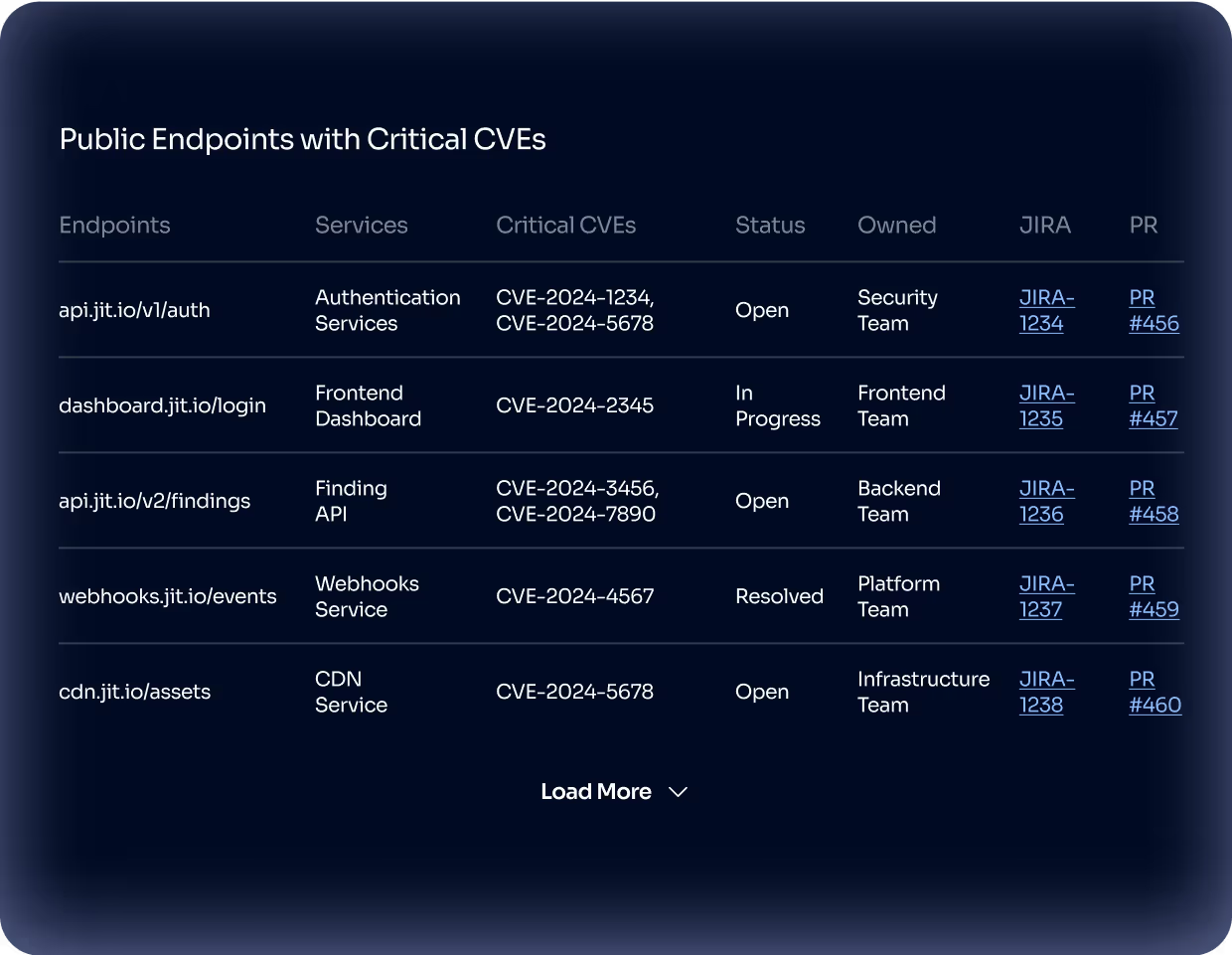
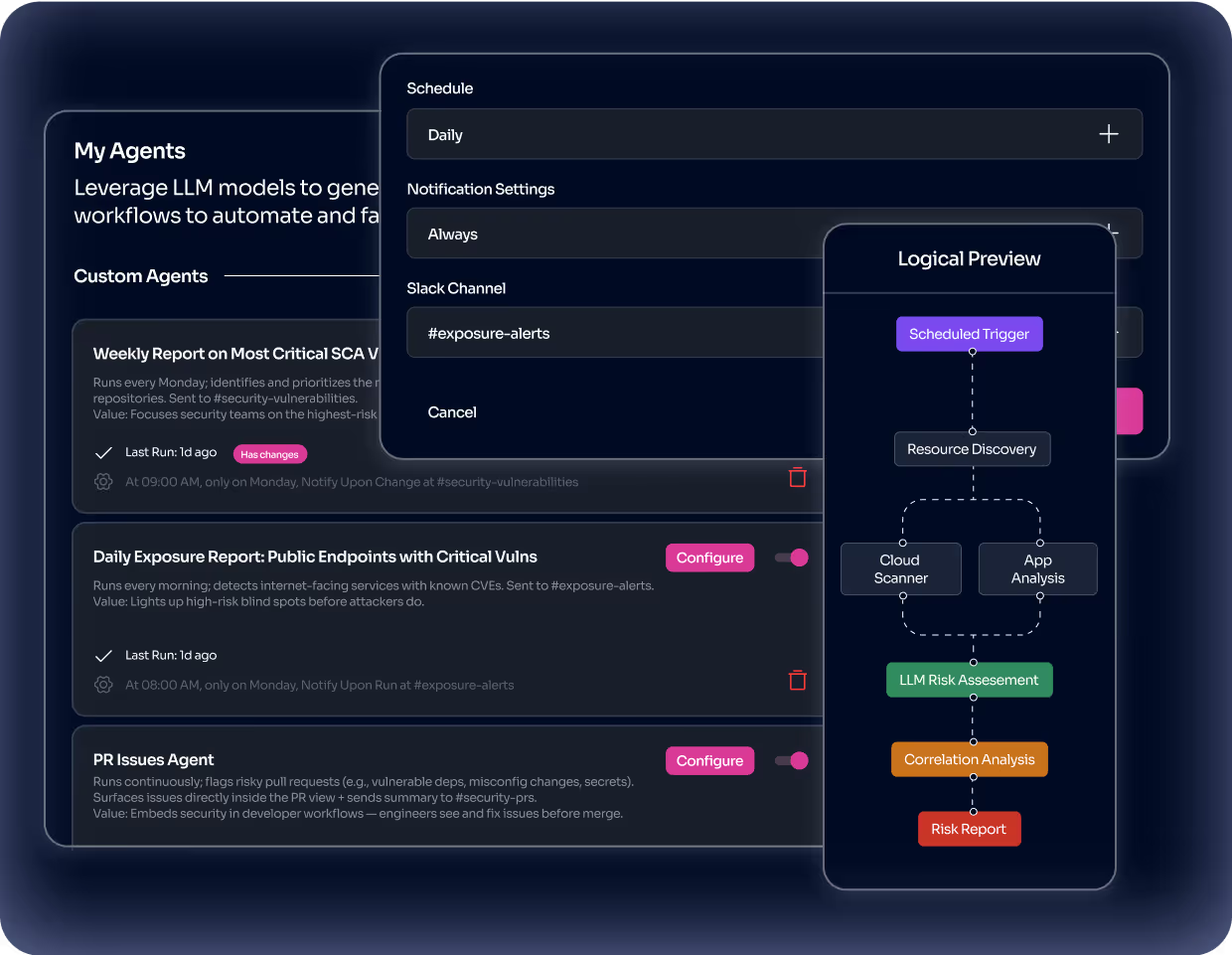
Create, modify, and save your Custom AI Agents to monitor risks over time
How do you know Jit’s Custom Agents produce accurate and relevant results?
Jit’s Custom Agents query your Company Knowledge Graph, which is automatically generated based on Jit’s integrations with your codebase, cloud environment, security tools, and documentation. They only return insights grounded in this graph, ensuring findings are accurate, contextual, and aligned with your environment, policies, and priorities.
Code-to-cloud-to-runtime integrations

30+ security scanners integrations

Internal policies + compliance reqs




