The 7 Essential Components for ASPM (Application Security Posture Management)
Updated February 19, 2025

AI Summary
As application development accelerates and product security vulnerabilities continue to increase, Application Security Posture Management (ASPM) has risen as a practical solution to prioritize the code and cloud security issues that matter most.
The limitations of traditional AppSec in the form of static scans and point-in-time tests leave organizations grappling with incomplete insights and noisy results. Developers are often left prioritizing vulnerabilities without meaningful context, which can lead to misdirected efforts and unresolved risks.
That’s why we have put together this definitive list of what sets ASPM apart from traditional AppSec or CSPM tools, and what you need to make sure your ASPM delivers before taking the plunge.
What is ASPM (Application Security Posture Management)?
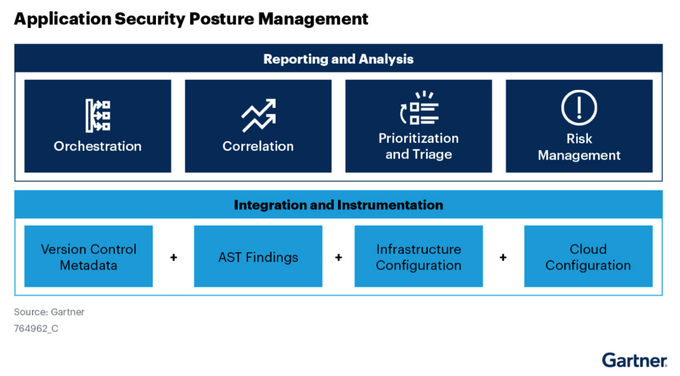
ASPM is a modern framework that provides continuous visibility, assessment, and mitigation of application-layer security risks. Unlike traditional AppSec tools, ASPM works across pre-production and production environments, combining application runtime context with business-critical insights to streamline risk management. Historically, we’ve likened this to a Developer Portal that doesn’t exclude security as part of the entire application lifecycle management and software quality.
This is because an ASPM platform integrates with existing CI/CD pipelines and AppSec tools, offering a unified view of vulnerabilities that doesn’t just surface issues—it prioritizes them based on factors like exploitability in production and potential business impact. This makes ASPM an essential component for organizations looking to scale their security operations while aligning with DevSecOps practices.
It operates on the application layer, overseeing applications in both on-premise and cloud-based environments to detect and address potential security risks. These solutions focus on applications in all environments from pre-production to production and complement the application testing tools throughout the CI/CD pipelines.
The traditional AppSec approach was a good option for software deployed on standalone computers. While AppSec tools can identify vulnerabilities during development and testing, they lack the context and continuity needed to manage risks dynamically. In this age of cloud-hosted software, a new approach that consolidates vulnerabilities across many different servers is required, one that makes it far easier to prioritize risk across your system.
Now you may be thinking, how does ASPM differ from other popular security tools and platforms, like a Cloud Security Posture Management (CSPM) for example?
A CSPM targets the underlying cloud infrastructure that the application runs on. This means, it ensures configurations, IAM policies, and data storage align with security best practices to safeguard cloud workloads. This is of course, an extremely important part of security, however, our approach at Jit is that the application eventually can’t be decoupled from the infrastructure it’s running on when it comes to security.
ASPM bridges this gap by continuously monitoring vulnerabilities, correlating them with runtime behavior, and providing actionable prioritization both on the application-level, and the infrastructure that is powering it. This approach ensures that security issues impacting critical business functions are addressed first––whether on the application or infrastructure layer, reducing noise and increasing operational efficiency.
| | AppSec | ASMP | CSPM |
|---|---|---|---|
| Focus | Point-in-time testing of applications for static and dynamic analysis to surface software vulnerabilities. | Continuous app vulnerability and security monitoring throughout the application lifecycle. | Continuous security monitoring of the underlying cloud infrastructure and configurations. |
| Scope | Application source code and pre-production environments. | All pre-production and production instances of the running application. | All cloud infrastructure components. |
| Use Case | AppSec use cases are limited to static and dynamic testing of applications as a preventive measure for mitigating security issues. | Covers a broader scope of security monitoring through continuous monitoring and triaging for proactive vulnerability management. | CSPM extends the ASPM use cases to include cloud workload configurations, IAM, and data encryption for end-to-end security observability. |
| Collaboration | Limited to development and testing teams on or before feature integration. | Continuous collaboration between development, operations, and security teams. | Extends the ASPM collaboration model by including IT and site reliability teams. |
Why ASPM (Application Security Posture Management), and why now?
One of ASPM’s core strengths is its ability to combine runtime data with business context for risk prioritization. Unlike traditional tools that simply flag vulnerabilities, ASPM platforms assess exploitability in production environments. For application security to continue being relevant and not bypassed by developers, it needs to move from being purely informational to actionable, without too much friction or cognitive load.
Shift left entered the scene to push for earlier finding and fixing of vulnerabilities, to try and prevent security vulnerabilities from reaching production. However with the growing and almost incessant flow of vulnerabilities––it is nearly impossible to fix all vulnerabilities. Laundry lists of vulnerabilities, even if they are high severity but unexploitable, cause developers to focus on fixing the wrong problems based on arbitrary scoring. This can lead to harmful attacks due to truly exploitable issues that are farther down in the backlog and remain unresolved.
Malicious code attacks like SQL injections (SQLi), Cross-Site Scripting (XSS), and Remote Code Execution (RCE) are increasingly challenging to protect against, mainly due to the sheer volume and diversity of applications.
For example, if a vulnerability exists in unused code paths or within a service behind strong authentication, it may not warrant immediate attention. ASPM tools consider such nuances, enabling teams to focus their efforts where it matters most. This context-aware prioritization allows organizations to shift their security strategy from reactive patching to proactive risk management, reducing time-to-mitigation and improving overall security posture.
By continuously monitoring threats and prioritizing vulnerabilities based on their risk, Application Security Posture Management plays a critical role in delivering secure software. It can enhance an organization's security posture across all application and cloud-based environments, leading to improved communication, team collaboration, and proactive risk mitigation processes.
Your Guide to the 7 Critical Functions Your ASPM Should Have
1. Application asset discovery and inventory management
Asset discovery is the first stage – you can’t secure what you don’t know exists. Asset management is crucial to establishing a foundational knowledge base about your application’s ecosystem, in order to build a catalog of every element contributing to its functionality. Asset discovery should be conducted regularly to reinforce the consistency of the application’s security posture and to ensure you are continuously providing maximum security coverage for your application.
This discovery stage aims to create a detailed inventory of the application's assets, components, and dependencies that can all pose risk and impact your application’s security posture. This inventory mainly comprises hardware, software, network elements, third-party platforms, and libraries. It also includes detailed documentation about configurations, runtime and network parameters, versioning, and other relevant information about the tech stack of the application.
2. Runtime awareness and risk assessment and prioritization
Risk assessment and prioritization enables you to proactively identify, assess, and manage application security risks and prioritize vulnerabilities based on their potential impact on the organization––what is often referred to as reachability and exploitability.
By integrating with AppSec tools, these solutions can prioritize vulnerabilities – some can determine whether a security issue is actually exploitable in production, so developers can focus on the highest impact findings, and not just flag endless amounts of issues that are neither reachable nor exploitable.
In addition, ASPM can assess code and configuration risks at various levels to ensure that applications adhere to internal coding guidelines and additional security hardening provisions to meet external regulatory requirements (stuff that developers hate to do), reducing friction in applying compliance-required security guardrails).
3. Integration with existing application security processes
The scope of ASPM starts at the application's development phase. It works with multiple AppSec tools focused on different development-related security checks to provide a bird’s eye vulnerability management dashboard.
In this way, it facilitates the integration of security into traditional application security processes, enabling organizations to identify, assess, and mitigate security vulnerabilities and manage risk more effectively. By embedding security checks directly into developer workflows—such as inline code scanning within IDEs, automated vulnerability assessments in CI/CD pipelines, and runtime monitoring in production environments—modern ASPMs enable teams to address vulnerabilities at every stage of the SDLC. This integration ensures that security is no longer an afterthought but an integral part of the development process, breaking down silos and unifying security efforts within a streamlined DevSecOps framework.
A bonus is the ability to integrate advanced security tools, such as DAST and IAST platforms that provide additional and deeper security checks.
4. Real-time monitoring and alerts
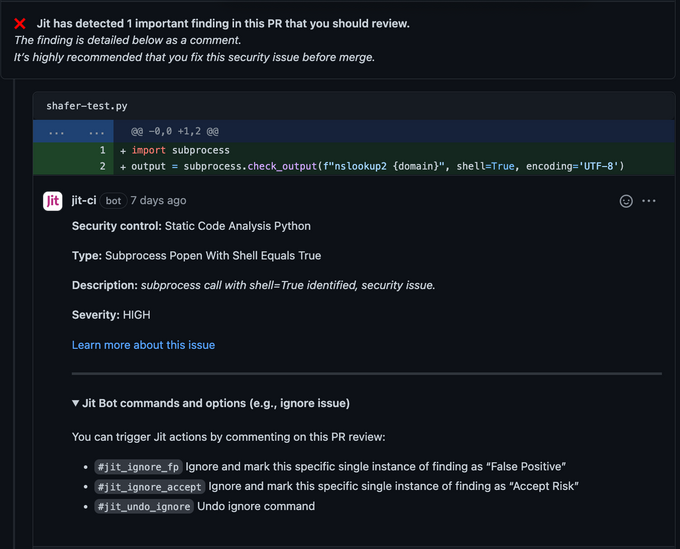
ASPM solutions provide continuous monitoring of applications in runtime environments, detecting new vulnerabilities, misconfigurations, or insecure access paths. This real-time visibility is critical for detecting and mitigating threats as they arise.
To monitor proactively and identify vulnerabilities, tool misconfigurations, and other potential weaknesses, ASPM must provide real-time alerts to the relevant teams when security issues are discovered.
Beyond just displaying alerts, these tools should conduct a consolidation, de-duplication, correlation, and risk assessment of alerts to convert noise into actionable insights. By consolidating and de-duplicating alerts, ASPM platforms transform noisy data into actionable insights, empowering teams to respond promptly.
5. Access management
Access management focuses on monitoring and controlling user access to the application. This access is enforced via Role-Based Access Control (RBAC) policies. Application Security posture Management tools monitor these policy configurations to ensure all users have appropriate privileges based on their roles and responsibilities while preventing unauthorized access.
For instance, ASPM can dynamically adjust risk scores based on anomalous behaviors, such as unusual API usage or unauthorized data access attempts. This contextual intelligence ensures a robust defense against evolving threats. Some examples of this contextual information include user location, time of access, historical access patterns, and network characteristics.
6. Reporting and Dashboarding
ASPM is all about a single source of truth about the application’s security status. An extensive reporting and dashboarding module helps organizations visualize and analyze the security posture of their applications at a central level.
Common security metrics to monitor include:
Count of vulnerabilities across code and dependencies;
List of misconfigurations, policy, and access violations;
Objective risk scores, like the security posture rating, which are based on the overall security compliance level of individual assets of the application.
A good ASPM platform should offer detailed reports on security incidents, vulnerabilities (including remediation action), risk assessment, security coverage for various assets, application testing, and security metrics, allowing security teams to get an overview of the current state of application security.
7. Compliance Monitoring
Compliance monitoring ensures that applications adhere to relevant security standards, regulations, and external policies. This is imperative in many industries and jurisdictions with specific rules and compliance standards that organizations must adhere to.
Application Security Posture Management facilitates compliance monitoring through a built-in security decision support system that:
Manages incident response planning, including devising custom incident response workflows and providing insights into historical incidents and attack patterns.
Automates technology stack assessment to ease the strategic decisions about selecting the right third-party tech components, such as frameworks, libraries, and platforms, based on their security performance.
Governs a system of continuous learning and improvement of security processes, including implementing new security standards and process adjustments.
While regulation and compliance processes many times add friction to developer processes, ASPMs can come in to significantly reduce the overhead and tick the boxes on technical requirements quickly.
It's time to fortify your Application Security
ASPM platforms have hard reset the way we do application security today, providing a framework that is much better equipped to secure our high-scale, distributed, cloud native world. Through incident response, streamlining compliance, and delivering proactive defense against myriad cybersecurity risks––they fortify applications against an ever-shifting threat landscape.
Jit’s developer-friendly DevSecOps platform was built to incorporate the principles of an ASPM tailored to modern engineering and cloud needs.Some of its unique benefits include its integration with a wide array of scanning capabilities that provide full SDLC coverage––SAST, DAST, and IAST tools. Jit then normalizes the output from disparate tools and consolidates security insights across the application lifecycle into a single and actionable dashboard.
ASPM’s real-time monitoring capabilities provide visibility into runtime environments, ensuring vulnerabilities are detected and prioritized based on their business impact. This includes tracking the application at runtime based on the deployment triggers to capture any vulnerabilities and insecure access paths. This feature ensures that the team has complete visibility of the security posture of the latest application release.
In today’s threat landscape, embedding ASPM early in the development phase is no longer optional—it’s essential. Jit provides a comprehensive DevSecOps toolchain that seamlessly integrates customizable application security checklists across coding, testing, and deployment, empowering teams to build secure applications without sacrificing speed or agility.
Learn more here.