Full Stack Security: Harnessing Open Source and Pro Tooling for Instant Protection
Updated May 15, 2024

AI Summary
With the rapid pace of technological advancements and the increasing sophistication of cyber threats, organizations must adopt a holistic approach to protect their product stacks from the code, through the infrastructure, security practices & culture, and even where the code is hosted through comprehensive GitHub security. Jit, from the onset has had the goal of enabling companies to achieve security instantly while keeping developer experience in mind and as a driving principle when embedding security. This is because if the security isn’t easy and native to developer workflows, it will be bypassed.
Part of the journey to delivering the most dev-friendly and rapid security coverage possible, was in building strong integrations and partnerships from the get-go with best-of-breed tooling. In this post, we will take a look at some of the newly introduced controls in the Jit ecosystem, where they come in to help provide full-stack security with a focus on three innovative tools—Semgrep Pro for SAST (Static Application Security Testing) or SCA (Software Composition Analysis) alongside advanced features, Trufflehog open source secret management, and the combination of Legitify and Aqua Security’s Chain-bench for GitHub security. All of these together are revolutionizing the way to safeguard product stacks end to end.
Semgrep Pro: Next Level SAST and SCA in the Jit Platform
Semgrep Pro is a paid commercial tool that is loved by developers for its reliable and wide security coverage of many programming languages that has recently been integrated into the Jit platform alongside its open source version to enable even more comprehensive SAST and SCA support. To leverage Semgrep Pro within Jit, a user simply needs to authenticate and will be able to unlock the ability to orchestrate the full range of Pro capabilities alongside Jit capabilities.
The Jit team has invested much research and development to augment Semgrep with AI remediation capabilities, which can automatically identify and address security vulnerabilities, as well as augment the current rulebase to cover novel security scenarios. This alongside the excellent and continuous work by the Semgrep team to stay ahead of evolving threats and the SCA capabilities only available in Semgrep Pro.
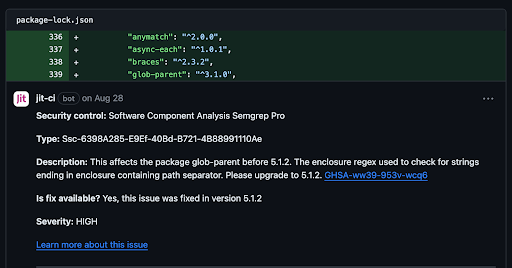
By using Semgrep Pro within Jit, you not only are able to receive the additional benefits of Jit like in-PR comments and remediation, scanning of other parts of the stack including cloud and dependencies, secret detection, but also all of the added capabilities only available to Semgrep Pro users. These include their best-of-breed SCA, proprietary rules, and multi-file scanning. Jit + Semgrep serves to enhance development velocity by making it easy to embed both SAST and SCA capabilities and receive filtered and curated alerts in developer workflows and pull requests for immediate and relevant remediation out of the box.
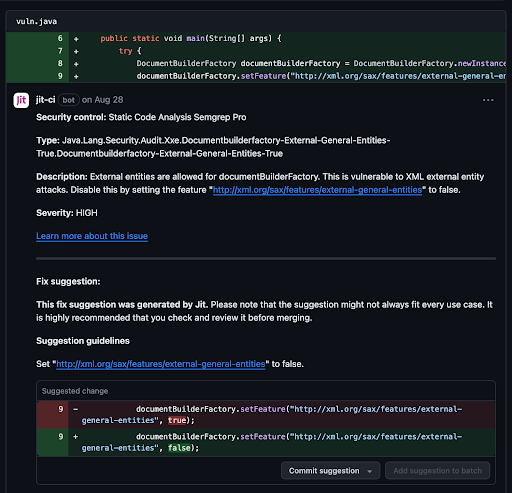
In the example below, you can see Jit alerting to vulnerabilities using Semgrep Pro (authenticated with a token).
You will find remediation suggestions that combine AI and Semgrep’s own out of the box suggestions, to help developers remediate issues in the code, and not only detect them.
Trufflehog: Open Source Secret Detection
Jit, from its early versions and as its default onboarding example, has provided secret security through the open source Gitleaks tool. Recently users have been indicating a growing interest in support for Trufflehog out of the box, so Jit set to work integrating it into the platform.
Trufflehog is an open-source tool that is gaining popularity for secret detection. It is very similar to Gitleaks but with a unique twist. Like Gitleaks, it scans everything that has been changed or added to a codebase in a pull request to detect hard-coded secrets, but the way Trufflehog does this is a little different. Trufflehog has a list of regular expressions for common services and third-party tools that integrate with our stacks, such as AWS, GCP, or Slack tokens. By doing so, Trufflehog will let you know if you accidentally or even intentionally uploaded a secret to the repository––for example, if you have a dev environment file with fake tokens for testing. This is where it gets interesting though, and where they have an added bonus that Gitleaks does not provide.
What truly sets Trufflehog apart is its ability to verify secrets by performing an API call to the specific service to check if this is an actual secret or just looks like one. This goes beyond the surface to determine if a secret is legitimate or not. This feature is invaluable for minimizing false positives, enhancing the accuracy of security assessments, and enabling developers to quickly assess risk.
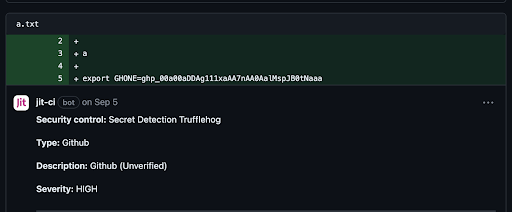
TruffleHog Example
Part of the Secret Detection plan, can be enabled by as-code overrides, which can be read in our docs.
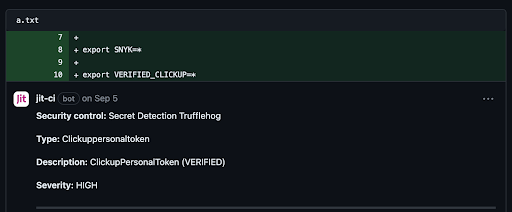
Below we can see VERIFIED tokens; tokens that were verified by TruffleHog as real, working tokens, which helps developers prioritize vulnerabilities. When they see a verified token detected, it means it’s not a dummy or fake token and should be immediately removed.
This is an example of a fake or unverified token.
Developers love this approach because it helps them to focus on critical issues by minimizing noise and verifying the legitimacy of secrets. This helps you to reduce exposure of secrets in PRs that might remain undetected, and also goes so far as to tell you whether a secret is verified or unverified and suggested next steps. Fun fact, the creator of Gitleaks, Zach Rice, recently joined the Truffle Security team, the company behind Trufflehog.
Legitify and Chain-bench: A Powerful Combination for GitHub Security
Legitify and Chain-bench combine forces in the Jit Platform to address GitHub security, such as misconfiguration and vulnerability management, making them essential components of full stack security. Oftentimes, we invest a lot of time and energy to secure our code, its composition, our infrastructure, and forget the most critical piece––where all of our code is actually hosted.
Jit has invested in research and development to curate the best features from each tool to provide the most comprehensive and accurate GitHub Security. The combination of Legitify and Chain-bench streamlines security assessments, freeing organizations from the burden of dealing with false positives. Through the dedicated GitHub Security plan, GitHub repository scanning is orchestrated through both excellent tools, making it easy to implement security best practices through hand-picked rules and eliminating the need to sift through noise, pinpointing issues such as dormant accounts or flawed branch protection rules. By merging the strengths of these tools, organizations can achieve comprehensive coverage of their repositories, safeguarding their most critical digital assets, source code, and configurations effectively.
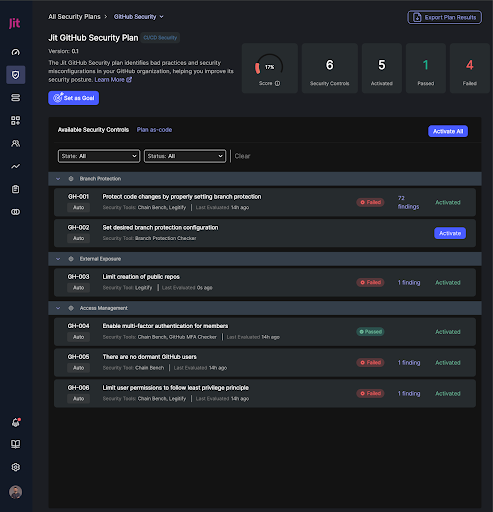
GitHub Security Plan
Below, you will find the layout showing the plan items the user can activate with a Personal Access Token from GitHub to enable end-to-end GitHub Security with Legitify and Chain-bench.
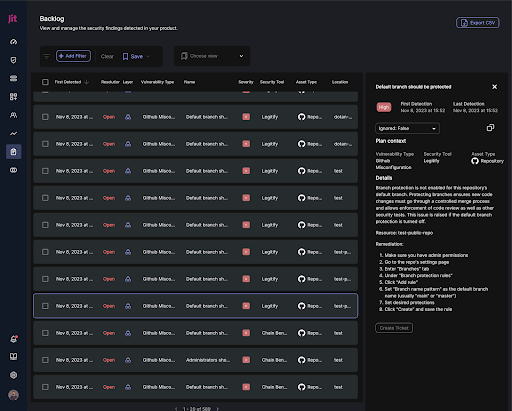
Here, you can see a backlog finding example from Legitify, which includes detailed remediation steps on how to solve an issue where the user does not have branch protection enabled. This is intended to protect their branch from unapproved or unauthorized changes that can open the door to unwanted security vulnerabilities.
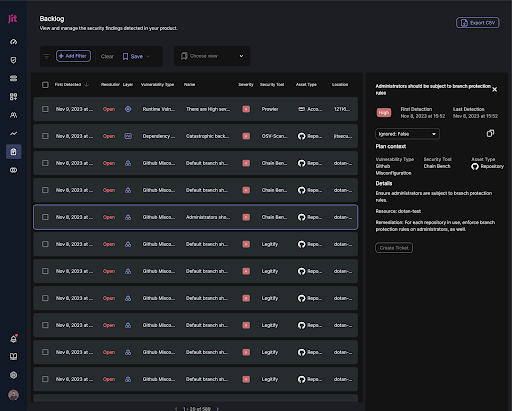
This Chain-bench example ensures that admins are subject to branch protection rules, to protect the default branch from being changed without the necessary guardrails and approval process rules such as code review, requiring checks to pass before approval of a Pull Request, and other best practices for repository security.
The Consolidation of Tools and Dashboards for Improved Developer Experience
Integrating new and popular tools into the Jit platform enables organizations to stay within the same ecosystem while benefiting from advanced security features that Jit provides, while consolidating dashboards and tools. Full stack security is no longer a luxury, but when it comes to end-to-end security, it's not just about the tools; it's also about the developer experience.
In an era where cyber threats are constantly evolving, security is non-negotiable, and you need to ensure that developers will not bypass the guardrails. Semgrep Pro, Trufflehog, and the combination of Legitify and Chain-bench offer organizations the tools they need to achieve wide security coverage instantly that are native to developer workflows. Through these integrations of tooling developers love, it’s possible for developers to focus on engineering processes, minimize security vulnerabilities and risk, and receive actionable alerts, remediation suggestions and in-PR fix suggestions without deviating from their typical workflows. This combination of wide security coverage coupled with developer experience will be the key to staying ahead of the rapidly evolving attack surface organizations face today, and ensuring that developers own security.