7 Principles of Secure Design in Software Development
Updated June 12, 2024

AI Summary
Cyber attackers have evolved beyond basic strategies like password-guessing and self-replicating code, adopting more sophisticated methods. Now, cyber threats are as sophisticated as ever, and traditional security measures are proving inadequate. The application security industry knows that the only way is left: shifting security left by embedding it directly into application design and development.
Up to 77% of organizations believe their application security could be improved, underscoring the prevalent gap in secure application development practices. Yet organizations find themselves at a crossroads, grappling with conflicting priorities and uncertainties about effectively integrating security into their well-established development lifecycles.
It’s unarguable that secure design can be a game-changer for software companies. But how do you move from contemplating the business value of secure design to implementing its principles in your software development process without disruption?
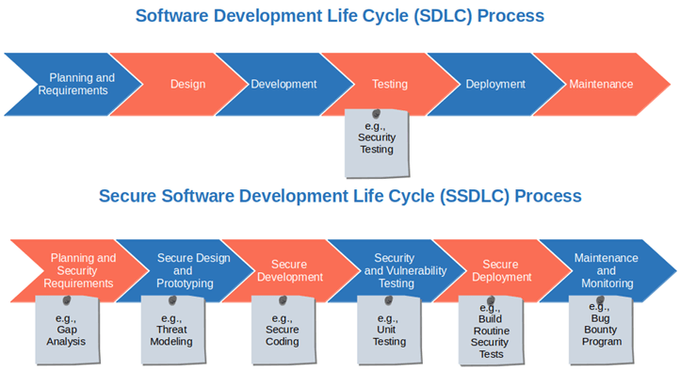
What does Secure Design in Software Development really mean?
"Secure-by-design" is an approach to designing and building systems with security in mind. It involves implementing continuous security practices, tools, and controls from the beginning of the software development lifecycle, ensuring that products are inherently secure. Embedding security measures early in the development lifecycle drastically reduces the attack surface for potential exploits – meaning products hit the market with a strong security posture.
At its core, secure-by-design is rooted in the DevSecOps philosophy – merging development, security, and operations. It helps to foster a culture of security awareness and responsibility across the teams - streamlining risk mitigation and vulnerability management. Though most commonly associated with software development, secure-by-design also applies to other domains, such as infrastructure design, IoT devices, and industrial control systems.
Code vs. Security – The Security-by-Design Imperative
In this fast-paced market, customers want a shiny new feature yesterday - not two months from now. Development teams are pressured to speed up their release cycles to push out new features and products ahead of their competitors. Amid this quest for speed, security becomes a steaming hot potato constantly being passed around between IT and DevOps teams. Nobody wants to get burned, but equally, nobody wants the security burden in their hands.
Secure-by-design bridges this gap between IT and DevOps - enabling teams to secure their software and enhance code quality from the start. This proactive approach to security leads to a more competitive security posture, reduces business risk, improves incident response capabilities, and ultimately translates to cost savings and faster market launches.
Embracing secure-by-design principles also simplifies compliance with frameworks like AWS FTR and standards like SOC2, which require businesses to show evidence of implementing various product security controls.
7 Principles of Secure Design in Software Development
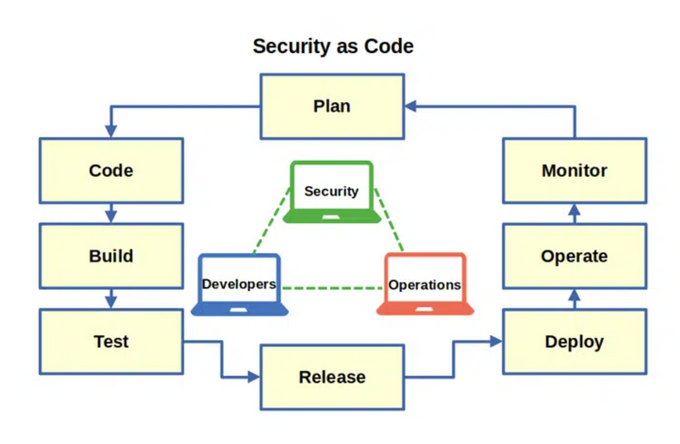
1. Security as Code
Security as Code (SaC) transforms security practices from manual processes to automated, scriptable components within the software development lifecycle. SaC involves writing scripts or predefined code templates to enforce security policies, performing vulnerability assessments, and automating remediation and security scanning processes.
Jit’s DevSecOps orchestration tool enables you to integrate and automate various open-source security tools. Operating directly within your GitHub or AWS environment, it allows you to secure every stage of the SSDLC and scan your code for vulnerabilities, hard-coded secrets, dependency concerns, and IaC misconfigurations. Plus, you can automate and manage all tools under one interface - reviewing real-time findings and remediation suggestions and solving vulnerabilities as they arise.
2. Secure Defaults
Adopting Secure Defaults is a fundamental principle that mandates systems configurations to be inherently safe. This approach stems from the understanding that many end-users stick to default settings. By setting these defaults to be highly secure, you can safeguard most users.
Secure Defaults could manifest in robust password policies, multi-factor authentication requirements, and even the default turning off extra services or features that could serve as attack vectors.
WordPress can serve as an illustrative example. Historically, specific versions of WordPress had default settings that were not security-centric, leading to widespread security flaws that left its millions of users vulnerable to attacks. Newer releases have since adopted more secure default configurations, such as unique database table prefixes and rigid password enforcement, significantly reducing the risk to users and the incidence of security breaches.
3. Least Privilege
The Least Privilege principle is a crucial best practice for Identity and Access Management (IAM). And it doesn’t just apply to users - every component in your system (machine identities such as resources and networks) should also operate with the least privilege necessary to perform its function. Adopting this approach reduces the potential damage of a breach by reducing the accessible attack surface.
Implement precise Role-Based Access Control (RBAC) configurations and regularly review and audit your system and user privileges. You can leverage automation tools to streamline this process, scanning for unnecessary permissions and suggesting revisions per the Least Privilege approach.
4. Separation of Duties
Separation of Duties (SoD) is about dividing tasks and privileges to minimize the risk of malicious activity or errors. No user should have a level of access that allows them to misuse a system on their own. For instance, in a CI/CD pipeline, the developer writing code should not be able to deploy it to production—this task should be assigned to a separate individual or system. Implementing SoD is technically straightforward but requires rigorous access control and workflow definitions.
5. Minimize Attack Surface Area
The Attack Surface Area (ASA) represents all the points where an unauthorized user can interact with a system or application. Minimizing ASA is about limiting these entry points, thereby shrinking the opportunities for adversaries to exploit vulnerabilities.
Developers should conscientiously assess and reduce non-essential code, services, and processes. For instance, during a server configuration, only specific necessary ports should be left open, while all others should be securely closed or blocked. API endpoints should also be judiciously created and avoid overly generic or wild-card endpoints that may expose more functionalities than intended. It’s equally imperative to deactivate and remove unused or deprecated features and components.
6. Complete Mediation
Complete mediation mandates that every access request to any system resource is thoroughly authenticated and authorized. This should happen every time, without exception.
Let's take an API in a microservice architecture as an example. Even if a user has been authenticated at the gateway level, each microservice should independently validate the user's permissions before fulfilling a request. This could be achieved by requiring a valid authentication token for every API call, with the microservice decoding the token and checking the user's permissions against the requested action.
7. Failing Securely
The principle of failing securely dictates that a system should respond to errors or failures in a way that preserves the overall security of the application. When something goes wrong, the system should default to a secure state rather than exposing vulnerabilities or sensitive information.
This principle involves implementing robust error handling and validation mechanisms throughout your codebase, ensuring that any failure, whether it's due to invalid user input, a system error, or a failed authentication attempt, results in a generic error message and does not leak any sensitive information or hints about the system’s internal workings.
Consider an authentication process as an example. If a user fails to log in, the system should not reveal whether the username was incorrect or the password didn’t match. Instead, it should simply indicate that the authentication failed.
Secure Design and Proactive Defense with Jit
The groundwork required to put secure design principles in place can feel overwhelming, but it’s worth planting the security seed now so you can reap its benefits as early as possible. Involve all the relevant stakeholders and plan a secure-by-design roadmap that considers each of these principles, as well as your own infrastructure and business needs.
Security automation tools are here to help, too. Jit’s DevSecOps orchestration platform integrates a wide range of powerful open-source security tools into your CI/CD and automates them to run for every PR. It covers your entire SSDLC for continuous security, including code, test, release, and runtime stages, requiring minimal effort from your team. Explore Jit now to see how you can best leverage it for your secure design goals.