When and How to Use OSV Scanner to Secure your Open Source
Updated June 7, 2024

AI Summary
We recently wrote about npm audit fix, which is an add-on to the excellent npm audit, that has become a fundamental tool for managing software packages in Node.js projects. However, developers working with other languages also require specialized tools for Software Composition Analysis (SCA). At Jit, our tool of choice for SCA scanning across a diversity of programming languages is OSV Scanner, a best of breed OSS solution maintained by Google. In this blog post, we'll explore the features, benefits, and applications of OSV Scanner when it comes to security and dependency management for many programming languages.
Why OSV Scanner?
OSV Scanner, maintained by Google, is renowned for its active development and high responsiveness to user feedback. With a dedicated team continuously pushing updates, fixes, and new features, OSV Scanner stands out as a reliable choice for SCA that many developers depend on. Continuously growing in popularity within the open-source community, OSV Scanner has gained a respectable (and well-deserved) following with numerous GitHub stars and contributions.
This is largely due to its versatility across languages and package managers. One of the standout features of OSV Scanner is its broad language support. Whether you're working with Python, Java, or other languages, OSV Scanner seamlessly integrates with various package managers and lockfiles (similar to what we described with npm audit fix, just for other languages besides Node.js). Where npm audit and npm audit fix stand out in the Node.js community––OSV Scanner shines for many other languages (side note - it also supports Node.js, npm audit though is a dedicated SCA for that ecosystem). Additionally, the tool frequently expands its support based on customer requests, ensuring compatibility with diverse development environments.
One of OSV Scanner’s greatest features is the comprehensive vulnerability database that serves as the backbone to its accuracy and speed. OSV Scanner’s logic is built upon an extensive vulnerability database, known as deps.dev, to identify and remediate security vulnerabilities. This database, which is also meticulously maintained and curated, includes comprehensive data from various sources including public vulnerability databases, security advisories, and community contributions, as well as metadata related to software licenses—a crucial aspect for compliance and risk management. Developers benefit from OSV Scanner's ability to suggest package version updates and provide actionable insights for vulnerability mitigation based on reliable information found in the deps.dev database.
License Scanning and Software Bill of Materials (SBOM) with OSV Scanner
In addition to vulnerability detection, OSV Scanner offers license scanning capabilities, enabling developers to ensure compliance with licensing requirements. By interfacing with the deps.dev vulnerability database, OSV Scanner provides valuable metadata, facilitating informed decision-making regarding software licenses and incorporation in software development projects.
License metadata provides important context for developers, as just recently we have seen many popular OSS projects make decisions to migrate licenses from open source to source-available licenses. On the other hand, some licenses may be overly permissive with copy-left permissions, and may expose your software to OSS implications that may impact commercial decisions.
OSV Scanner offers more than just vulnerability scanning; it also enables the vulnerability scanning of Software Bill of Materials (SBOMs), a critical component for managing and securing software supply chains. OSV Scanner provides a comprehensive overview of the software's security posture. With the SBOM generated, the OSV Scanner then queries the OSV database or other vulnerability databases to find known vulnerabilities that match the components listed in the SBOM. It checks against known vulnerability identifiers (e.g. CVE IDs) and other criteria.
Another great feature is OSV Scanner’s ability to align and integrate with other industry standards like SPDX and VEX. SPDX (Software Package Data Exchange), is a standard format for communicating software component information. The OSV Scanner data can be leveraged to generate SBOMs in SPDX format, allowing for easy integration with tools and systems that support SPDX. This helps ensure compatibility and facilitates the exchange of SBOM information across different platforms.
In addition, the OSV Scanner is also interoperable with VEX. VEX (Vulnerability Exploitability eXchange) is a document format that is growing in popularity and support among open source frameworks. It is designed to communicate the exploitability of vulnerabilities within a specific operational context. OpenVEX, a project led by the OpenSSF Foundation (the Open Source Security Foundation - another open source initiative that Google is highly invested in), is a tool built to standardize the format of these documents, making it easier for tools and systems to generate, consume, and share exploitability information. The OSV Scanner's output can be used as input for tools that generate VEX documents, aligning with the goal of providing actionable vulnerability exploitability information.
Jit 💜 OSV Scanner
At Jit, we leverage OSV Scanner to enhance software security, as well as compliance. First, it’s integrated to enable code scanning leveraging some of the most popular programming languages in our ecosystem. In addition, this support is constantly growing and evolving based on our users’ needs and feedback––and only recently greater support was added such as support for the Java package manager Maven, based on growing demand.
Another great feature is the license scanning that augments the code scanning capability. By utilizing its license scanning capabilities, Jit is able to identify and flag potential licensing issues within dependencies.
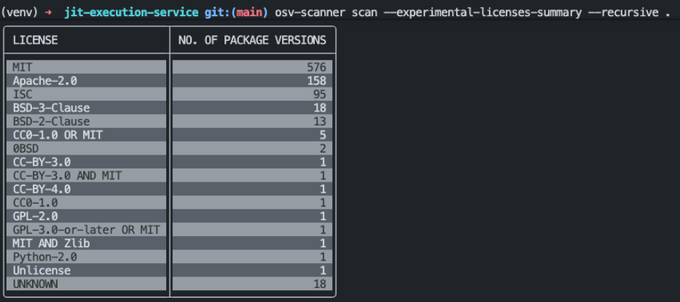
In the above screenshot we use osv-scanner to scan a local repository’s licenses and we get a table summary of the licenses used in our project.
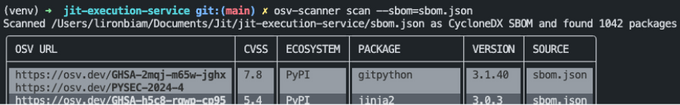
Below is an example of scanning an SBOM report for SCA vulnerabilities with osv-scanner:
TL;DR - OSV Scanner and You
As developers, we love our favorite programming language with an intensity that can drive us to flame wars of cultish fervor that will go down in the history books. That is why OSV Scanner is particularly handy, as it is a useful tool providing robust security for a wide breadth of programming languages, with the same unwavering quality, which is particularly useful for developers in polyglot environments who don’t want to have to qualify several OSS tools for the same job.
OSV Scanner makes it possible for developers to fortify their applications and code against security vulnerabilities and licensing risks while integrating with best of breed ecosystem tools and standards to further improve security posture. With its many features, comprehensive vulnerability database, license scanning, integration with ecosystem standards and formats, OSV Scanner stands out as a reliable tool for developers to painlessly align with engineering security and compliance policies without breaking a sweat.