How to Run an API Scanner with OWASP ZAP
Updated September 8, 2025

AI Summary
API exploits are rampant. 91% of organizations suffered API-related problems in 2021. Rogue endpoints are usually the root cause of issues experienced, and they are often caught too late - when an attack has occurred, and issues allow the attack to bubble up to the surface.
From unauthenticated API endpoints to accidentally deployed APIs - OWASP ZAP can identify and help prevent a potential catastrophic accidental data leak through the ZAP API scanner. This article guides you on how to run an API Scanner with OWASP ZAP so you can protect your software from API attacks.
While ZAP is an excellent tool for scanning APIs for vulnerabilities in runtime, it can be difficult to set up and manage yourself. For a fast and easy way to deploy Dynamic Application Security Testing (DAST), check out Jit's configuration wizard, which deploys ZAP in a few simple steps.
What is the ZAP API Scanner?
If you're responsible for API security, you know that it can be challenging to keep track of all the different API endpoints and ensure they're all secure.
Enter ZAP, the OWASP Zed Attack Proxy. ZAP is a free and open-source tool that can help you scan APIs for vulnerabilities. API Security is critical for any organization that exposes its data and services to the outside world. OWASP ZAP can help you scan APIs for vulnerabilities and potential attacks.
How can you use ZAP to scan APIs?
Using ZAP is simple. First, you need to configure it to work with your API. This configuration involves specifying the URL of your API and any authentication parameters that are required. Once you've done this, you can launch a scan of your API by clicking on the "Attack" button.
ZAP will then attempt to find any vulnerabilities in your API. If it finds any, it will report them to you so that you can take steps to fix them.
It does this by scanning and attacking the application and looking for known security issues. The benefits of using the Zap API scanner are that it can find and direct you toward methods that can help fix vulnerabilities that would otherwise be difficult to find, and it can do so automatically. This can save developers a lot of time and effort and can help to improve the security of their applications.
You can use ZAP to scan APIs for the following types of vulnerabilities:
- SQL Injection
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Server-Side Request Forgery (SSRF)
- Insecure Direct Object References
- Insecure Cryptographic Storage
- Failure to Restrict URL Access
You can also use ZAP to attack web applications and APIs in the following ways:
- Brute force attacks
- Dictionary attacks
- Web application firewalls
- Web application scanners
Running an API Scanner with OWASP ZAP, step-by-step
1. Installing the add-ons
You can extend the functionality of OWASP ZAP with add-ons by going to the marketplace and selecting one of the tools available.
To get to the marketplace, click on “Manage Add-On, " located on the icons toolbar underneath your main navigation bar. This will bring up a dialog containing all the tools you can download and install from the marketplace. You can also manage already installed tools.
You can use the filter to check if you’ve got OpenAPI support installed. If it is installed, OpenAPI support will appear under the installed tab. If not, OpenAPI will appear under the Marketplace tab.
2. Importing via the UI
When you have OpenAPI support installed, it will allow you to import a GraphQL Schema from a File in the import menu. Selecting this option will open up a new dialog where you can specify the relevant file or URL to import.
3. Importing via the API
You can also import via the API by setting definitions from URLs and local files. To do this, check out the API Web UI. Navigate to Local API > openapi. It will give you the option to either import via file or target URL.
4. Spidering
When you use the OpenAPI add-on, it automatically detects any relevant API definitions. The automatic detection will aid the spidering process and help it explore the definitions. The spider will only limit itself to the scope of the URL, and any additional domains are considered out of bounds.
5. Using the API scanning script
ZAP supports scripting languages such as JavaScript, Zest, Groovy, Kotlin, Python, and Ruby to let you define rules, targets, and triggers.
Writing your own API scanning script can help you target specific areas of an API, allowing you to fine-tune the attack.
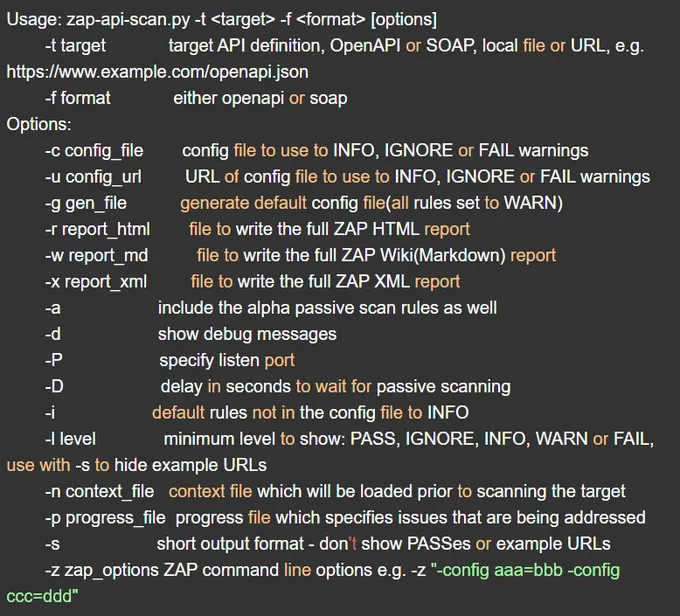
6. Command line options
When writing your script, OWASP ZAP has a list of command lines that lets you fine-tune your scanning needs. Here are the commands that you can use for your script:
7. Scan rules
Scan rules define scripts. This sets the boundaries, and by default, OWASP ZAP OpenAPI will disable rules that are clientside based. Instead, it will add two additional rules to the scripts: alerts on HTTP response code errors and alerts on unexpected content types.
The parameters for these rules and fine-tuning can be done through the configuration file. Defaults in the configuration file are appended with -g. The baseline configuration file for the API includes both passive and active scan rules.
Changes to the configuration file for passive and active rules are treated differently. When you modify a passive rule, it will only affect how the scan results are reported. Active rules are skipped over if they are flagged with IGNORE because passive rules are quick to run, while active rules can be time-consuming.
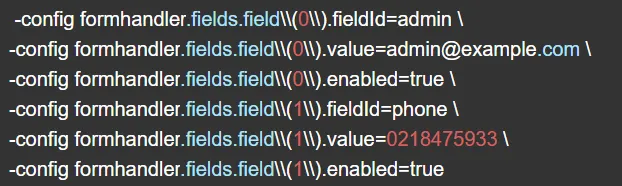
8. Specifying values
ZAP will always have default values to kickstart you off. However, if you want to set your values, you can do this via the ZAP command line option. Here are some example definitions:
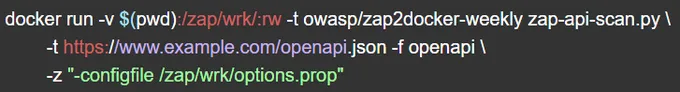
If you are using ZAP through a Docker instance, you will need to use the -z script option. This option allows you to use a specific property file rather than manually determining the specific values you need. Here is an example of the script:
9. Authentication
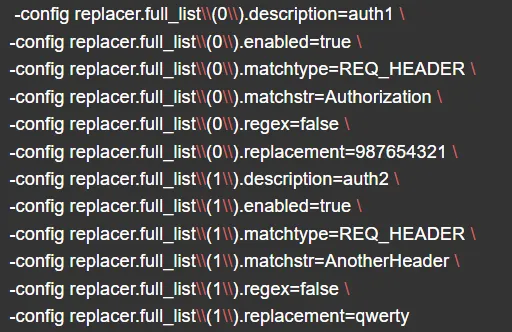
When APIs are protected by an authentication mechanism, you can use header values to obtain the necessary and applicable tokens. To do this, you must tell ZAP that there are things to retrieve and store temporarily.
Here is a set of example commands to help you out.
The above will replace the specific authorization headers with your one.
Automating the safety of your APIs with Jit
Security is necessary for any commercial and enterprise application. We need to automate app security to find and fix security vulnerabilities in apps before they are deployed to production.
OWASP ZAP is a fantastic tool for finding vulnerabilities before they become problematic. With Jit, you can easily integrate with OWASP ZAP and other crucial security tools to build a minimum viable security plan that protects your entire pipeline. Interested in giving us a go? Book a demo today.