IaC Security Essentials: How to Code Your Way to a Fort Knox Infrastructure
Updated November 5, 2024

AI Summary
Infrastructure as Code (IaC) is selling like hot cakes in IT provisioning and administration. One of the core components of DevOps and the “shift left” movement, IaC enables the codification of infrastructure while reducing overhead and increasing environment consistency.
The flexibility and agility it offers are unprecedented. When mistakes don’t happen in the process, that is. More than half of all successful breaches result from human error or misconfigurations. Infrastructure engineers and senior software developers are humans, too - so they’re bound to make mistakes at some point. But could the security gaps in IaC be more of a curse than a blessing for cloud-native infrastructure?
Ensuring your IaC is protected from malefactors takes rigorous planning, and it starts with understanding where potential security risks lie. This article guides you through the security considerations of IaC and how you can best mitigate risks to maintain a strong-as-steel infrastructure.
It’s an IaC revolution, but where does security fit in?
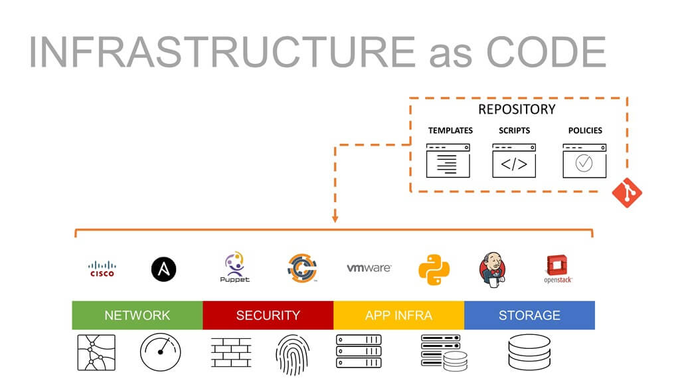
IaC is a powerful tool for deploying, managing, and scaling complex IT processes without impacting development velocity. It offers a flexible approach that turns application infrastructure management and provisioning into something they know well - declarative code scripts.
From a cloud-native application security perspective, IaC also improves the security of cloud-native deployment by solving environment drift in release pipelines. It enables consistency by replicating preconfigured templates and employing auditable version control - much like software. So, it’s no wonder that as many as 58% of IT decision-makers are adopting IaC.
However, as the saying goes, with great power comes great responsibility. There are several risks to consider when adopting IaC as an alternative to manual configuration processes, including:
1. Insecure handling of code secrets
Code secrets like passwords, API keys, or IP addresses of critical server systems and webhook URLs in IaC templates and scripts pose a risk if exposed to malefactors.
2. Configuration drift and “shadow” assets
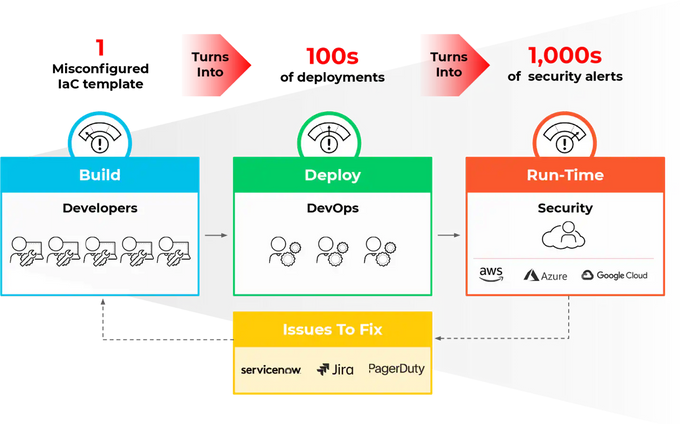
The security of your IaC depends on the immutability and consistency of your infrastructure. When developers directly change the infrastructure and bypass pre-deployment security scans, you get configuration drift between your environments and potentially untagged and de-facto invisible cloud infrastructure.
3. Untrusted base images and misconfigured templates
To codify infrastructure, developers employ IaC templates that include base images. Base images from an untrusted source can include malware and backdoors. Moreover, IaC template code and its dependencies may contain bugs - like any code. These bugs can become security risks if not identified and remedied before deployment.
4. Human error
The IaC risks mentioned above, and many more, are most commonly caused by human error rather than malice or technical malfunction. With development velocity prioritized above all else in rapid and agile development processes, it’s far too easy to grant overly permissive access to a service to speed things up or make manual changes to the production environment infrastructure.
IaC Security Essentials: How to Code Your Way to a Fort Knox Infrastructure
1. Adopt DevSecOps and GitOps practices
DevSecOps, a set of practices for adding a layer of security to the DevOps workflow, can help automate IaC security while minimizing interference with developer workflows. Make your infrastructure build scripts part of the codebase and treat it as such throughout your CI/CD pipeline through Security as Code. This helps you ensure that all infrastructure changes are scanned, tested, verified, and deployed uniformly and securely.
Moreover, using GitOps for IaC versioning, you can track IaC configuration changes more quickly. This also creates an audit trail and enables better collaboration on IaC security issue remediation in a developer-native environment.
2. Perform IaC security scanning
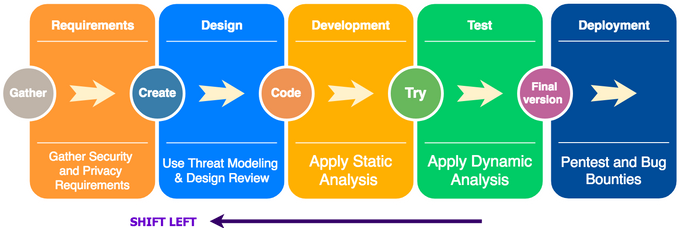
Automated security scanning of code and application assets in the CI/CD pipeline is one of the core concepts of DevSecOps. You can only do so much to prevent misconfigurations and security vulnerabilities from popping up in your code. However, there’s quite a lot you can do to detect these issues in the early stages of development and runtime.
This entails integrating Software Composition Analysis (SCA) tools and Static Application Security Scanning (SAST) of your IaC. You can leverage battle-tested open-source tools like KICS, an IaC scanning SAST tool that can handle Terraform, Serverless Framework, Pulumi, CloudFormation, and AWS CDK output. For runtime IaC security, you can employ Prowler to scan for misconfigurations and vulnerabilities in the construction of cloud resources.
Jit’s DevSecOps platform can orchestrate KICS and Prowler (and many other open-source security tools such as SCA and SAST) straight into your CI/CD pipeline. Plus, it provides developers with enriched findings for each vulnerability discovered and instant remediation suggestions for over 200 IaC misconfigurations.
3. Enforce Least Privilege and harden access management
The principle of least privilege (PoLP) should be the cornerstone of your Identity Governance strategy. Following this principle requires limiting permissions to a minimum and granting access only when needed. Create strict IAM policies and continuously monitor user activity to ensure no access control gaps.
You can also employ and enforce rules like key auto-rotation, temporary access roles, or Role-Based Access Control (RBAC). RBAC can help you implement mandatory and discretionary access control, restricting network access based on roles and striking the right balance between security and operational efficiency.
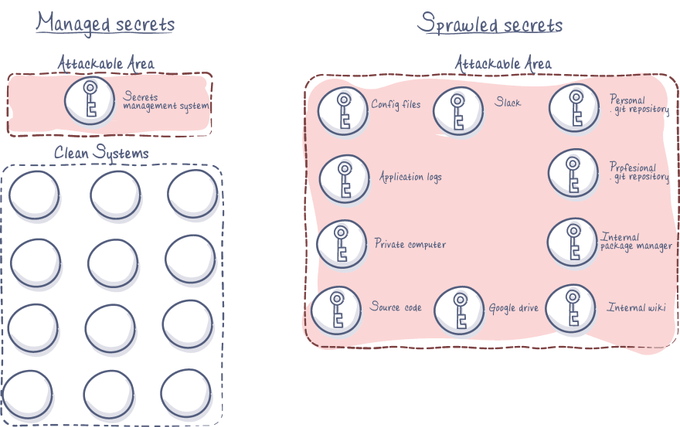
4. Prevent code secret sprawl
Even though code secret privacy is one of the most common best practices for application development today, some secrets can still leak unintentionally and fall into the wrong hands. Another type of scan you should employ are code secret scans to ensure your IaC configuration files don’t contain potentially sensitive information like passwords and API keys.
You can include open-source tools like Gitleaks in your IaC security scanning policy using the Jit DevSecOps platform. In addition, it’s worth looking into vendor services like AWS Secrets Manager and Microsoft Azure Key Vault.
5. Train your devs & prioritize IaC security
The only way to minimize human error and reap the security benefits of IaC is through training and prioritization of code security on an organizational level. This requires a security-first mindset and entails bridging the operational and conceptual gaps between information security engineers and software developers.
With security awareness training and proficiency in organizational security policies and tools employed, developers are better equipped to deliver safe code - including the code that builds the infrastructure.
6. Employ continuous monitoring
Monitoring of infrastructure for changes in IaC template configurations can help increase visibility into your overall cloud security posture. But more importantly - continuous security monitoring tools can alert you to configuration changes and environmental drifts in your infrastructure, as well as necessary updates and patches you should apply to the third-party resources you use in your IaC setup.
7. Codify your policies
Infrastructure is not the only thing you can codify to streamline operations. By using policy as code (PoC), you can define, manage, and enforce infrastructure security policies through code, enabling you to automate the implementation of organizational policies and best practices for security and compliance in your infrastructure code.
IaC security orchestration with Jit
Infrastructure as code enables developers to build and deploy scalable infrastructure securely. It minimizes human error and misconfigurations that stem from manual management and provisioning of application infrastructure. However, IaC introduces its own set of risks and potential vulnerabilities that can expand your attack surface.
As with any type of code, the key to secure development is integrating security into the SDLC with tools that empower developers rather than overburden them. Jit is a continuous security tool that streamlines the integration of security controls throughout the DevOps workflow with a cloud-native CI/CD approach. We leverage proven open-source libraries and tools to create a developer-friendly, insight-enriched DevSecOps orchestration platform that you can get started with right away. See how it works.