How to use the OWASP Application Security Verification Standard (ASVS) to Protect Web Applications
OWASP ASVS provides helpful guidance for application security. Let's break down its structure and practical use cases to incorporate this standard into your security program.
Updated September 8, 2025

AI Summary
Global online content has soared dramatically since 2020 - with the average daily usage being close to 7 hours. For more than a quarter of their day, every day, your customers are generating important data such as personal details and card information.
App users may not often think much about the data they provide. But for malicious users - all this data is a digital goldmine held by businesses like yours.
On average, SiteLock reports that sites experience approximately 94 attacks every day. More than 22 billion records were exposed in 2021.
These attacks have put a spotlight on application security. But how can you ensure you're focused on the right risks when maintaining and securing your application?
The OWASP developed the OWASP Application Security Verification Standard (ASVS) to answer this question. Let's explore this standard for guidance on how to protect your web application and safeguard your data.
What is OWASP ASVS?
The OWASP Application Security Verification Standard is an open application security standard that provides a framework for assessing the security of web applications and services.
The goal of ASVS is to help organizations establish a level of confidence in their applications' security and identify and mitigate risks. The guidelines include a set of security requirements that you can use to assess the safety of web applications and services.
These requirements cover many security concerns, including authentication, authorization, data security, session management, and code vulnerabilities that jeopardize application security.
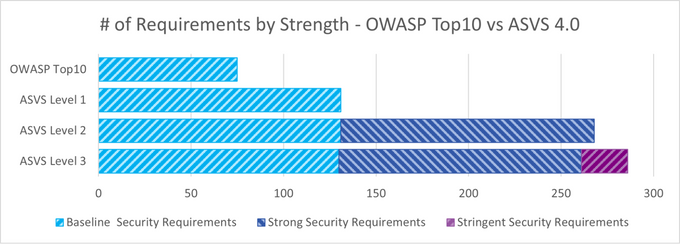
Application Security Verification Standard 4.0 updates
The latest version of the Application Security Verification Standard - 4.0 - was released in March 2019 and is regarded as the gold standard for security requirements as it covers both traditional and modern architectures.
Significant changes include the removal of Level 0, meaning that security expectations are baked into an application from the start.
The updates also provide a new baseline to prevent vulnerabilities from being pushed to production. It suggests minimal checks to surfaces potential security issues from being developed.
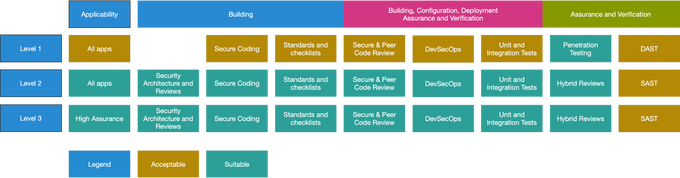
Understanding the different levels of ASVS
Different types of applications will have varying security requirements. Security "levels" are a helpful way to prioritize security requirements based on the amount of resources you have, and which data your applications are handling.
- Level 1 - Basic provides the most basic level of security and is typically sufficient for small applications with low-security risks. Application Security Verification Standard Level 1 is often assigned to applications that don't handle sensitive data, which makes them less of a target for attacks.
- Level 2 - Standard provides a higher level of security and is typically required for applications with medium security risks. This often includes apps that conduct transactions or handle sensitive data that can be leveraged for financial gains by malicious users. Level 2 is usually assigned to applications susceptible to injections, validation, and authentication-based attacks.
- Level 3 - Advanced provides the highest level of security and is typically required for applications with high-security risks. Level 3 requires the highest level of protection and contains highly sensitive information such as personal details, finance, and legal documents. For Level 3, security is often integrated at the beginning of the application pipeline, right through to production deployment, with automated monitoring as a secondary precaution.
Each level inherits requirements from its predecessor. For Level 2 requirements to be satisfied, Level 1 requirements must also be satisfied. Similarly, for software to comply at Level 3, it must also comply at Levels 1 and 2.
The structure of the OWASP Application Security Verification Standard
The official 4.0 version is split into 14 chapters and covers everything you can potentially encounter regarding software development.
From architecture designing and threat modeling requirements to API and web services verification, each of the 14 chapters targets a specific area and provides a comprehensive cyber security risk assessment checklist at each level.
Chapter 2 covers authenticator verification requirements, which include:
- Password security
- Authenticator lifecycle
- Credential storage
- Look-up secret verifier, amongst others.
Each of these subsectors contains a description of the requirement and a checklist explaining required tasks for organizations to complete. Some tasks are relevant for all levels, and others are only for Levels one or two.
How to use OWASP ASVS to protect your web application
Here are four key ways the guidelines can assist in protecting your web application:
Enhance your security performance metrics
You can use these guidelines to measure your organization's progress in implementing application security controls and identifying areas where additional work is needed.
By using these guidelines as a security performance metric, organizations can more easily find gaps in their security controls and plans and ensure these are improved promptly.
Using OWASP ASVS as a guide to ensure security can also be beneficial for your reputation. OWASP does not provide certifications to any vendor, verifier, or software, as it is a not-for-profit and vendor-neutral organization.
Meeting this standard means that your customers can trust your application and know that their data is handled safely.
Knowledge and guidance
OWASP Application Security Verification Standard can be used to improve security knowledge and provide security policy development guidance. In addition, it can be used to educate developers, ops teams, and anyone involved in the software development lifecycle about best security practices.
The standards and requirements under each chapter can bring awareness to security knowledge gaps and ensure that your software is developed with best practices in mind.
During procurement
Organizations often struggle with assessing the security of the products and services they procure.
The OWASP Application Security Verification Standard can be used during the procurement assessment process to provide a comprehensive, standardized list of security requirements that can be used to verify the security of products and services.
You can include ASVS reports in a Request for Information (RFI) or Request for Proposal (RFP) that vendors can use to assess their products and services.
These guidelines allows organizations to quickly compare the security of different products and services and make informed decisions about which to procure.
Agile projects
This standard can be used to secure agile projects by providing a comprehensive checklist of application security requirements that can be used to guide the development process.
It can also supplement other security measures and help ensure security is built into the agile development process.
The 14 chapters highlight areas that require security at each agile development phase, such as the application's design, implementation, and deployment. The goal is to help ensure that the application is secure before it is deployed.
Using Jit to implement OWASP Application Security Verification Standard
The ASVS standard provides helpful security guidance for those looking to benchmark their processes against best practices. However, deciphering and implementing the recommendations in these standards can be complex and time-consuming.
Jit streamlines the process of integrating these guidelines into your SDLC with our OWASP ASVS Security Plan, which provides the relevant security controls out-of-the-box.
Specifically, by simplifying the implementation of OWASP ZAP tools and other code security tools, you can get up and running with a full toolset to cover these guidelines in a matter of minutes.
From there, you can report and monitor progress toward completion as you implement these controls and resolve security risks.
Learn more about Jit's Security Plans here.


![AWS FTR (Foundational Technical Review) Checklist [XLS Download]](https://entail.jit.io/en-assets/jit/fit-in/280x280/Security_Standards-1747040330047.png)



