Top 7 Web Application Security Tools
Updated August 19, 2025

AI Summary
‘Who would look under the doormat for my keys?’ is an assumption we make when we ‘hide’ the keys to our home. It is the same logic we extend to vulnerabilities hidden in our web applications. Yet, these are low-hanging opportunities for attackers.
70% of web apps show severe security gaps like a lack of WAF protection and basic encryption, making them a funfair for vulnerabilities. With threats like injection attacks, broken access control, and cryptographic failures surging, now is a good time to explore web application vulnerability scanners.
What are Web Application Security Testing Tools?
Web application security testing checks websites and web app elements to spot potential security weaknesses. It crawls networks, databases, and application codebases to identify vulnerabilities that attackers can exploit to raid the sensitive data in your web application. Some of the most common vulnerabilities that web app scanners protect against include SQL injections, cross-site scripting (XSS), malicious code, and misconfigurations.
You can operate these scanners manually or automate them. In automation mode, they crawl your application on a schedule, analyzing input fields, forms, and other website elements. This is ideal for routine scans and contributes to maintaining a secure-by-design system. Manual web application security testing is typically used for in-depth assessments, enabling you to interact more directly with the application.
Benefits and Challenges of Web Application Security Testing
Web application security testing tools provide a systematic and automated way to uncover known and unknown vulnerabilities across all your web apps. While static analysis tools also scan your cloud estate looking for vulnerabilities, they often return even the most minor issues that may not be real risks. The key benefit of a web application vulnerability scanner is its ability to reduce false positives to near zero. If you see an alert from a web application vulnerability scanner, you know it needs your attention, or something is seriously at risk.
Many industry-specific regulations, such as PCI DSS for the payment card industry or HIPAA for healthcare, mandate regular security assessments to identify and address vulnerabilities. Web application vulnerability scanners help you demonstrate regulatory compliance by assessing your web apps systematically. Plus, the detailed reports you get from your scanners can be used as evidence in audits, showcasing your proactive security measures.
Despite these benefits, a web application vulnerability scanner can be notoriously difficult to configure due to many factors:
- The complex tech landscape: With every passing day, organizations add new technologies, programming languages, dynamic content, and open source and commercial tooling to their cloud estate. This makes every system a moving target that’s hard to scan thoroughly.
Authentication and authorization bottlenecks: Many risks lurk in the shadows of legitimate identities and permissions. They can be hard to spot as they look and even behave exactly like genuine users - internal or external.
Keeping pace with today’s threats: A web application vulnerability scanner can start becoming outdated as soon as it is implemented. As threats become more mature and hard to spot, dev teams must update their security scanner continuously.
Key Features for Web Application Security Testing Tools
Accuracy and Low False Positives
If your tool flags a vulnerability that doesn’t exist, it will send the team on a wild goose chase, burning time and resources. Web app security testing is generally great for ensuring low false positives, because it finds results in the runtime context of the application.
Automated Scanning and Scheduling
A web app security testing must monitor your website or app and its assets without human assistance to ensure continuous and (relatively) low effort risk detection and remediation. It should also allow you to schedule the crawling sessions for continuous monitoring. Using a security orchestrator like Jit, you can easily schedule and automate all your web app scans.
Integration with Development Tools
Your scanning tool should seamlessly integrate with:
- CI/CD pipelines to trigger scans based on new deployments
Development tools like code repositories and integrated development environments
Security tools like web application firewalls, audit tools, and penetration testing tools
Project management tools like Jira
These integrations ensure continuous security testing and facilitate collaboration between development and security teams.
Reporting and Remediation Guidance
Web application security testing must provide rich and insightful reports to track progress over time and highlight recurring gaps. It is to give you an easy-to-understand view of your website performance once a scanning session is completed. The tool must also produce steps to guide you in addressing the issues raised.
Top 7 Web Application Security Testing Tools
1. Jit
Jit unifies web application security testing with many other security testing methods. Jit’s platform centralizes web app security testing alongside SAST, SCA, secrets detection, CI/CD security, and cloud security. Each of these tools are integrated into the SDLC with a single click, and deliver results to developers entirely within their PR, so they never need to leave their environment.
For web app security testing specifically, Jit simplifies configuration and deployment for ZAP via a unique configuration wizard.
Best for
Those looking for an easy way to implement web application security testing and a complete developer security toolchain into the SDLC.
Customer Review:
“I love the notion of Jit providing as-code security plans, which are minimal and viable. The fact that Jit also automates the selection of relevant security tools and unifies the experience around them is super valuable.”
2. ZAP
Zed Attack Proxy (ZAP) is a free, open-source web app scanner that offers features like anti-CSRF (Cross-Site Request Forgery) tokens, authentication and authorization, and an alert mechanism. It is managed by OWASP's strong security engineering community and receives regular feature updates. Jit significantly simplifies the configuration and deployment for ZAP so security practitioners can get started quickly.
Best for
Security professionals and developers looking for a best-in-class open-source scanner.
Customer Review:
“Easy to install, run, and interpret the results. OWASP ZAP helped me to achieve standards of security testing. The fact that it is an open-source project is just incredible. The documentation is written well and comprehensive.”
3. Wapiti
Wapiti doesn’t focus on source code to identify security flaws; instead, it crawls deployed web pages and looks for error messages and irregularities. It employs a fuzzer technique to automate security testing using invalid or random information as inputs to see if a script is vulnerable. Testers use Wapiti to detect vulnerabilities like file handling errors, database injection, and cross-site scripting.
Best for
Identifying risks by attacking scripts and sending payloads to trigger errors.
Customer Review:
“Very well done. We have been looking at tools to help secure web applications. They were either obnoxiously overpriced or did not have the flexibility we sought. This has, so far, been quite easy to use and take the information to secure the applications properly.”
4. W3af
w3af primarily addresses OWASP's Top 10 vulnerabilities present in your website. It comes with a GUI (Graphical User Interface) framework and can also be used with w3afconsole, a command-line interface. It uses black-box techniques and plugins to conduct web application security tests for over 200 threats, such as XSS, Injection, LFI, RFI, and CSRF.
Best for
Penetration testing using open-source alternatives.
Customer Review:
“The tool is modular and extensible. It has garnered over 2000 GitHub stars, and its source code is readily available.”
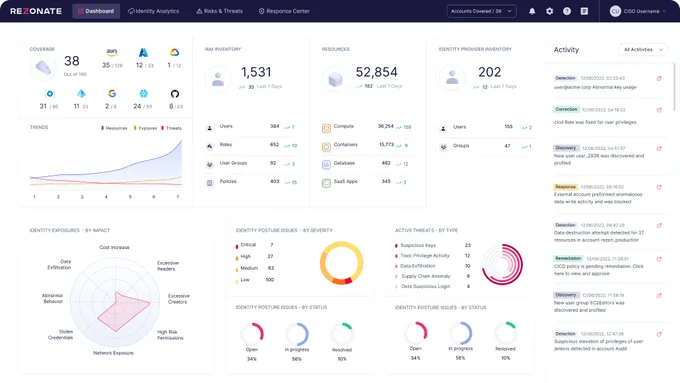
5. Rezonate
Rezonate scans your web app to discover and profile the human and machine identities accessing it. It dives deeper into each identity to spot potential flaws within your web applications’ permissions and authentication and helps you mitigate risks throughout the identity management lifecycle. Rezonate gives you a helpful risk score for your web application’s security, which can be a benchmark for tracking progress over time.
Best for
Gaining visibility over what identities are accessing what in your web app and preventing IAM-based threats.
Customer Review:
“By embracing the dynamic cloud and applying that same agility towards its security, Rezonate is changing the way cloud security is thought of today.”
6. Spectral
Spectral evaluates your web application’s code, configurations, and other source code elements to identify risks such as exposed API keys and cloud misconfigurations. It automates the scanning process along with safeguarding secrets at build time. It is also a language-agnostic solution that is compatible with 500+ different stacks. With this wide compatibility, Spectral can keep pace with the changing landscape of web application frameworks and technologies.
Best for
Securing web apps from data breaches due to secrets mismanagement.
Customer Review:
“Integrates easily into ADO, allowing us to track down exposures we previously had no knowledge about.”
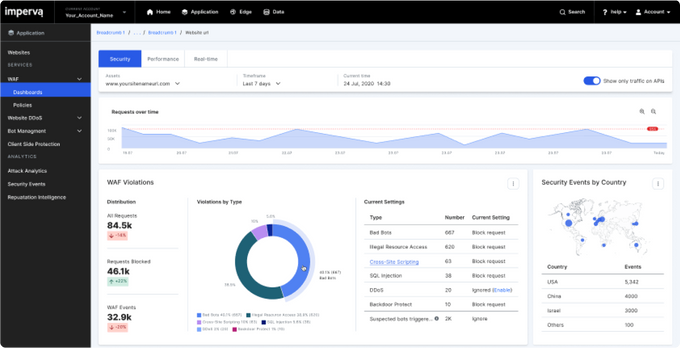
7. Imperva
Imperva is a SOC solution particularly effective against OWASP's Top 10 vulnerabilities. Imperva’s Scuba Database Vulnerability Scanner can scan your web application for over 1000 vulnerabilities per industry standards and offers protection from zero-day attacks.
Best for
Automating policy creation and implementation.
Customer Review:
“It is very easy to use, and its scan policy builder and website adding process is very easy; just a couple of clicks and it's done.”
Next Steps for Strengthening Web Application Security Testing
Web application security testing is often a core component of modern application security strategies. While tools like static application security testing (SAST) and software composition analysis (SCA) can catch vulnerabilities as developers are coding, they probably won’t catch everything and many of their results will be false positives. With web application security testing, you know most of the results will represent real risks.
Configuring web application security testing is notoriously complex, especially when combined with all of the other tool sets needed to round out your application security strategy. That's why we built an out-of-the-box security toolchain at Jit, which automates implementation of SAST, SCA, secrets detection, cloud security, and web app security scanning in a few clicks. Check it out for yourself.