Announcing Jit’s SBOM: Map all Dependencies in Minutes
Published October 7, 2025

AI Summary
We’re excited to announce Jit’s Software Bill Of Materials (SBOM), which automatically identifies, maps, and categorizes all open source components and third-party dependencies within your repos in a matter of minutes. Jit also shows the related open source license for each third party component, providing an instant overview of open source legal risk.
While the software supply chain is critical for modern application development, tracking security and legal risks associated with hundreds of third-party software components is a logistical nightmare. Jit SBOM solves this problem with a click – immediately improving trust and peace-of-mind in your software supply chain.
Jit unifies SBOM with many other security tools – including SAST, SCA, secrets detection, CI/CD security, IaC scanning, cloud security, and DAST – providing a single view of code-to-cloud security.
Book a demo for complete visibility across your third party software components.
Why we built SBOM
When the Log4j vulnerability took over the security and developer communities in 2021, everyone had the same question: does my system rely on open source components and dependencies that expose this vulnerability in production?
While it may seem like a simple question to answer, anyone running an application in the cloud knows otherwise. Modern cloud applications are built on thousands of open source components and dependencies to dramatically reduce busy work for engineers. Without these essential components, developers would have to build their services from scratch.
While third-party software components aren’t going anywhere, neither are the software vulnerabilities consistently found within them.
Since these components are often publicly available, malicious actors can predict attack paths for applications containing sensitive data and act accordingly.
For this reason, modern software development teams need a continuously updated list of third party components in production. With Jit’s SBOM, this requirement is entirely automated.
In addition to security threats, third party software can also introduce legal risk. Open source software components have different licensing requirements that specify how the open source can be used. Jit’s SBOM specifies the license for each open source component in use, so engineering teams can quickly spot potential legal trouble.
How to implement Jit SBOM
Once you’ve connected Jit to your repositories (this takes minutes), go to the Jit app and simply select “SBOM” in the left menu, and hit “Activate”.
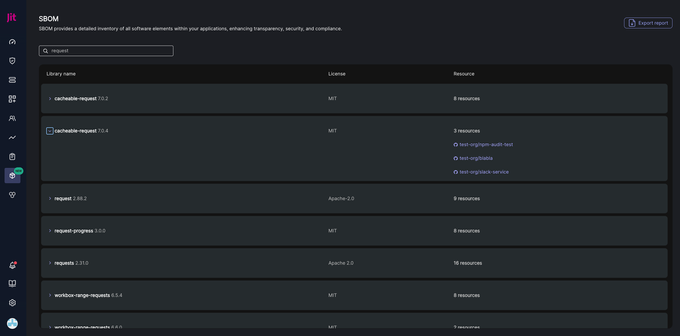
As Jit scans your repositories, SBOM will begin populating with third-party components in your repositories and their associated open source license.
From here, you’ll have a complete view of your third-party dependencies and open source components. Next time vulnerabilities in open source repositories are announced, you can immediately determine if you’re exposed.
Curious to try it out? Book a demo today.