Top 10 Infrastructure as Code Security Tools for 2026
Updated June 9, 2025

AI Summary
Infrastructure as code is the Usain Bolt of software development. By treating infrastructure provisioning and management as code, teams can deploy entire infrastructures with the click of a button and easily modify or extend their IaC to meet business and user needs. This speed, agility, and scalability are unprecedented.
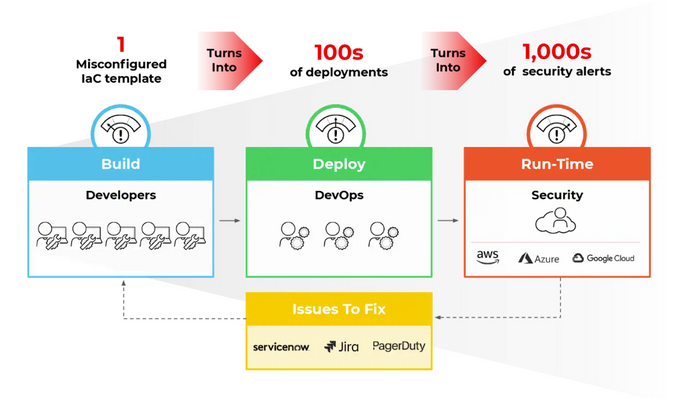
But there’s more to this button click than meets the eye. The more you automate, the more likely you will leave behind security gaps like misplaced lines of code or misconfigured settings. There were 10 million hard-coded secrets detected in public GitHub commits in 2022, a staggering 67% rise from 2021. While not exclusive to IaC, hard-coded secrets can risk exposing sensitive data and opening secure systems to unauthorized access.
Securing IaC to preempt such common vulnerabilities starts with embedding security earlier in the development pipeline. Luckily, you don’t need to do this alone - and certainly not manually. There are a myriad of powerful IaC security tools that can help you reap the ground-breaking benefits of IaC safely.
Top 10 Infrastructure as Code Security Tools in 2026 at a Glance
- Best overall infrastructure as code security tool in 2026: Jit
- Best tool for automated CI security testing: KICS
- Best IaC security tool for teams using Terraform: TFLint
- Best tool for teams needing AWS security compliance: Prowler
- Best for pre-deployment checks across IaC & cloud platforms: Checkov
- Best for seamless workflow integration: Spectral
- Best for teams that use containerized applications: Trivy
- Best tool for multi-IaC, cloud-native deployments: Terrascan
- Best tool for comprehensive cloud security beyond IaC: PingSafe
- Best IaC security tool for cloud-focused organizations: CloudSploit
What Is Infrastructure as Code Security?
Infrastructure as code (IaC) security analyzes the scripts and code that automate your cloud infrastructure setup to find vulnerabilities. It's a technical discipline crucial in a DevOps environment that aims to confirm that your deployments are not only operational but also fortified against threats.
In the current landscape, where cloud-native technologies and dynamic provisioning are the norms, IaC security has become critical for operational integrity. Minor misconfigurations in IaC – such as incorrect access permissions or exposed sensitive data – can leave the door wide open for an attack. IaC security tools are the watchful eyes that catch these mistakes, often before they turn into more significant problems.
Key Features to Look for in IaC Security Tools
There are many different IaC security tools to choose from, each with their own pros & cons, but you should focus on tools that offer the following key features:
- Static code analysis for IaC files: Scans Terraform, CloudFormation, ARM/Bicep, and Kubernetes YAML before terraform apply or kubectl apply, flagging risks like public S3 buckets, overly permissive security groups, or pods running as root.
- Static and dynamic analysis: A robust IaC security strategy demands both SAST to analyze code before deployment and DAST to assess the running environment after deployment. Jit integrates both SAST tools and DAST tools, providing comprehensive coverage that scrutinizes your infrastructure for vulnerabilities at every SSDLC stage.
- Policy-as-code enforcement: Uses engines such as OPA/Rego, HashiCorp Sentinel, or builtin rule sets to codify controls (e.g., mandatory encryption or MFA-enabled IAM roles) and fail CI jobs when templates violate them.
- Drift detection & runtime comparison: Continuously compares the committed IaC state to the live cloud footprint, alerting on manual changes or compromised resources so teams can re-apply or remediate.
- Multi-cloud coverage: Supports AWS, Azure, GCP, on-prem Kubernetes, and hybrid stacks, normalizing findings so one policy file secures every provider and reduces tool sprawl.
- CI/CD & Git integration: Provides Git pre-commit hooks, GitHub Actions, GitLab runners, or Jenkins steps that scan PRs and block merges of risky templates, keeping GitOps pipelines clean by default.
- Remediation guidance: Generates inline fix snippets or auto-opens pull requests with corrected HCL/YAML, helping developers resolve issues quickly without hunting through docs.
Top 10 Infrastructure as Code Security Tools for 2026
The Benefits of IaC Security Tools
IaC (Infrastructure as code) security tools offer significant advantages by bringing uniformity and automation to your infrastructure deployments. Key benefits include:
- Standardized and secure deployments: IaC security tools enforce security protocols automatically, ensuring that all infrastructure deployments are consistent and meet defined security standards. This makes your infrastructure more scalable and manageable.
- Version control integration and easy rollback: Tightly integrated with version control systems, these tools provide a clear history of all infrastructure changes, not only enhancing transparency but also allowing for easy rollback to a previous secure state if issues arise.
- Proactive drift detection and cost savings: IaC tools vigilantly monitor for configuration drifts and discrepancies, swiftly flagging issues before they escalate. This preempts problems, significantly cuts down on remediation costs, and helps manage data security.
- Streamlined compliance and auditing: IaC security tools make it easier to report on your security posture and audit your systems. This is a major benefit for both internal governance and external regulatory compliance, as they help you demonstrate adherence to essential security standards and frameworks such as PCI, SOC 2, and HIPAA.
Securing Your Code for the Future
The critical role of IaC security in modern infrastructure management is clear. The right tools elevate not just security measures but also the efficiency and synergy of development and operations teams. As we look to the future, investing in such solutions is not just a matter of security – it's a matter of ensuring the resilience and efficiency of our infrastructures.
Jit’s DevSecOps platform not only integrates with but also amplifies the capabilities of other top IaC security tools. It is an end-to-end automation solution that enables you to easily integrate various security testing tools (such as IaC, DAST, and SAST) into your CI/CD pipelines so you can fully manage your entire SSDLC security under one platform. Explore Jit today to secure your infrastructure.