What is Shift Left Security and 7 Steps to Get Started
Updated December 31, 2024

AI Summary
In today’s fast-paced, cloud-native world, software engineers are empowered to do much more than just write code. The linear structure of traditional security assurance processes owned fully by information security teams is no longer effective or efficient, creating bottlenecks and delays in software delivery.
As such, DevOps teams are shifting left many IT functions like infrastructure provisioning and testing. However, 44% of development professionals still consider security teams primarily responsible for application security, while 49% of security professionals put this responsibility on their development team’s shoulders.
This disconnect between developer and infosec workflows hinders developer productivity. Plus, it makes security no man’s land - which isn’t a great place to be considering the growing number of cyberattacks across development and production stages.
So what is the solution? An approach that makes code and application security assurance a joint cross-departmental effort - also known as shift left security.
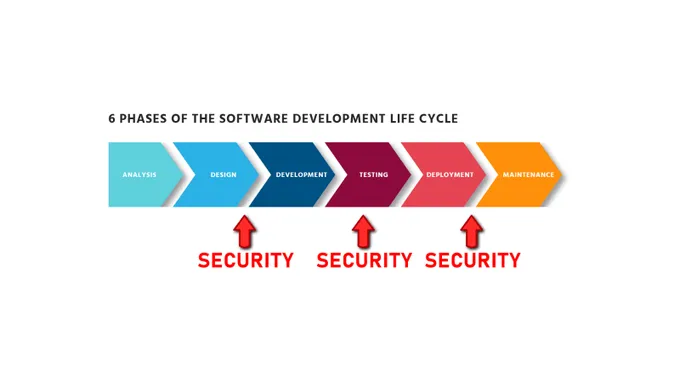
What is shift left security?
Shift left security (or shifting security left) is an approach to application security with an emphasis on detecting and addressing security issues as early as possible in the SDLC through Security as Code practices.
Coined by Larry Smith in 2001, shifting left is a general term for integrating quality assurance in software development processes. When applied to cybersecurity, shifting left entails breaking down organizational and technological silos between security and development teams and enabling quick and smooth resolution of security issues earlier in the deployment timeline through effective collaboration.
It’s worth noting that, contrary to common misconception, shift-left security is not about making developers experts in security and compliance tools and practices or placing them in charge of all things application security. Instead, this approach empowers software engineers by providing them with knowledge and tools (think SAST, DAST, and SCA security solutions) to prevent and mitigate security issues in their code. Similarly, it provides infosec teams with effective feedback loops for resolving issues discovered at any stage of the SDLC.
When right is wrong: why you need to shift security left
You can’t shift left something that doesn’t have a strong foundation on the right. Shifting security left is best implemented as part of an organization-wide cybersecurity strategy that enables integration and collaboration across teams, departments, and the C-suite. So, why are businesses shifting security left?
Higher efficiency
2023 is set to be a record-breaking year for supply chain attacks. With the increasing frequency and severity of cybersecurity attacks, developers are pressured to mitigate risks faster and more efficiently. Shift-left security not only enables developers to spend less time chasing urgent security bugs but also saves businesses money, allowing more time for innovation. With more automation and fewer pre-deployment barriers, developers can produce secure code more efficiently and effectively without increasing technical debt.
Reduced costs
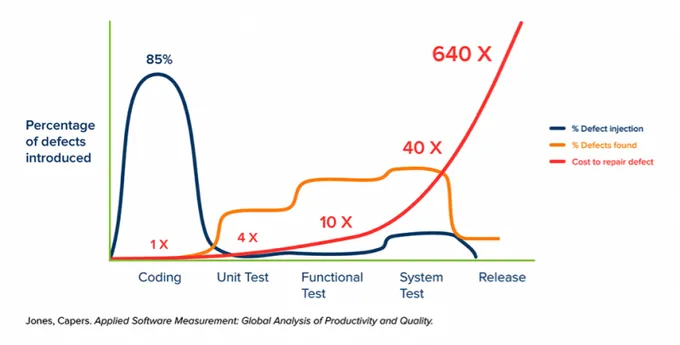
Waiting for the later stages of development to detect and repair security issues can result in costly fixes, even if the vulnerabilities that made it onto public-facing servers are not exploited in a breach.
Some studies suggest that the cost of repairing defects at later stages of the SDLC can be as high as 640 times the cost of repairing them at the development stage. This is especially true if the system needs to be taken offline to wait for highly critical fixes (costing the business money) and when you need to make in-depth architectural changes to address the threats.
Faster time-to-market
Discovering security issues further down the delivery pipeline causes more delays in delivery than their discovery and remediation at the early stages of the SDLC. Problems detected in source code scanning are much easier and faster to fix than issues discovered after release. They are also less likely to cause significant setbacks in your planned delivery timeline.
Improved customer trust
With fewer vulnerabilities reaching production environments, you get fewer potential breaches. If your application is deemed risky, you are in danger of losing the trust of your customers. Ensuring your app is safe is especially critical in highly regulated industries like financial services and government contracts.
7 Steps to Get Started with Shift Left Security
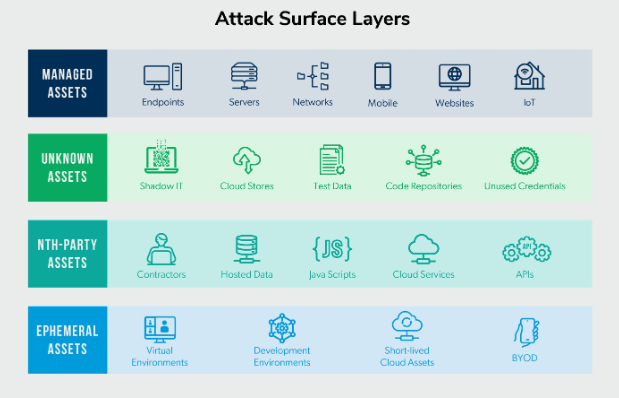
1. Assess your SDLC and attack surface
Before you can shift security left, you must have a complete understanding and in-depth view of how and where code moves from the developers’ minds to production. This process should involve documenting how software flows between people, devices, and third-party services.
Once you’ve documented the flows, processes, and third-party vendors that may be involved in developing and delivering your applications, you can plan your attack surface management strategy to begin to find and fill the security gaps. At this point, it’s also essential to understand how code and application security assurance are managed today and where in your pipeline you test for vulnerabilities.
2. Ensure a collaborative security feedback loop
Promoting a DevSecOps culture throughout the organization and including development, operations, and security professionals in the distribution of tasks and responsibilities in the security feedback loop is vital for the success of any shift-left security initiative. By promoting communication and empathy among the participants in securing your SDLC, you can design a process of collaboration that is fast, clear to all participants, and doesn’t create bottlenecks or friction.
3. Automate security testing
The importance of automation in shifting security left cannot be overstated, and it can prove to be a “quick win” for your shift-self security strategy. You can integrate SAST and DAST, Interactive Application Security Testing (IAST), Runtime Application Self Protection (RASP), secret scanning, and dependency inspection into your CI/CD process while employing battle-tested OSS solutions like Semgrep.
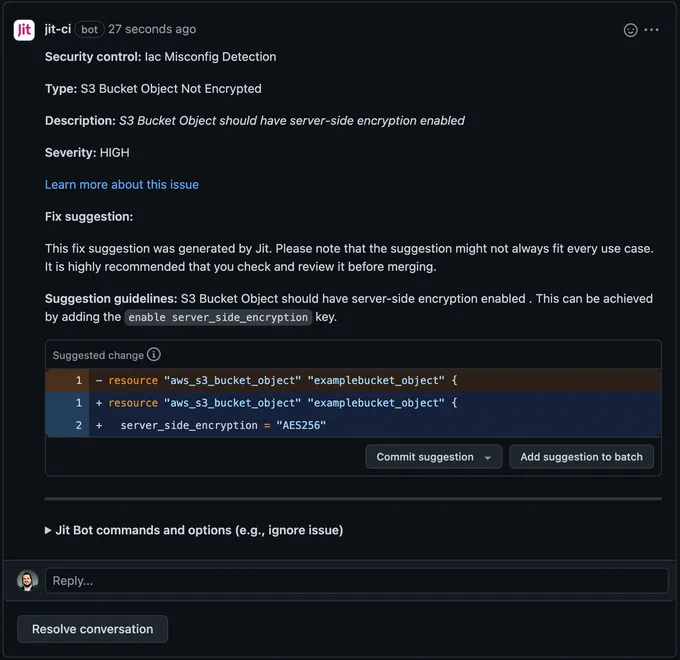
Jit can integrate with various open-source security tools to automate all security testing across your CI/CD. Moreover, with Jit’s DevSecOps orchestration platform, you can enable automatic remediation for common vulnerabilities and misconfigurations. In those cases, the suggested fix is displayed to the developer in the PR itself, and they can accept or reject it with a single click. Here’s an example of Jit’s remediation suggestion in GitHub:
4. Train your teams in secure coding standards
While 85% of companies have a security awareness and training program, 56% of leaders still believe their employees lack security knowledge. Shift-left security entails a shift in responsibilities among product, development, security, and operations teams and, as such, requires continuous and practical training to ensure everyone can rise to their responsibilities. For developers, it’s essential to instill secure coding standards through cybersecurity awareness training and guidance.
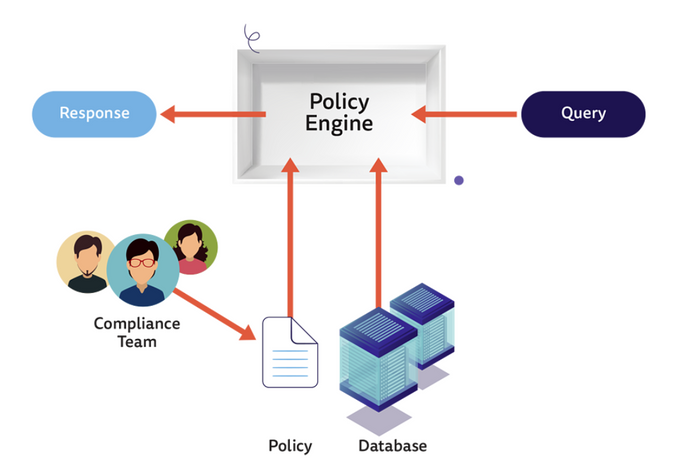
5. Embed policies and guardrails into your pipelines
At its core, shifting security left focuses on empowering and enabling software developers to secure their applications better. Offloading some tasks from security teams to automation through Policy as Code allows these teams to speed up deployment and remediation.
Creating and automating security policies in your pipeline will enable you to set consistent boundaries and guardrails in which developers can operate freely and deploy more secure code with no added effort or changes to their workflows. Here’s a simple graphic showing how Policy as Code eases policy enforcement through automated rules and conditions:
6. Keep detailed documentation
Storing detailed and updated documentation of code changes, security measures, and threat assessment is critical, especially as you add new security solutions to your toolchain. Thorough documentation enables your team to promptly address issues, maintain quality assurance, and contribute to team-wide knowledge sharing. Plus, regulations like SOC2 require rigorous control and documentation standards, so this practice will make it easier for you to adhere to and prove that you meet such regulatory controls.
7. Measure and optimize
Shifting security left is not a “set it and forget” ordeal. Technologies and threats change, new tools are introduced to make your job easier, and your SDLC and application codebase scale and grow. Much like CI/CD, shift left must be a continuous process of measuring success and optimizing to match business needs and constraints.
Shifting left with Jit’s DevSecOps orchestration
One of the challenges with shifting security left is choosing the tools and processes to fit seamlessly into existing development operations without overburdening developers with unnecessary tools and uninformative alerts.
Jit is a unique DevSecOps orchestration platform built with developer experience as a top priority. With Jit, you can create a security plan that provides only the protection your SDLC needs. A turnkey solution to automating security testing with OSS tools and none of the hassle, Jit morphs and grows to match your shift left strategy. Explore Jit to discover how to shift left security the right way.