SAST vs. DAST - Picking the Perfect Protector for Your Web App!
Choosing between DAST vs. SAST tools for app security doesn't have to be a never-ending dilemma. In fact, why choose at all?
Updated May 17, 2024

AI Summary
Innovation requires continuous integrations, delivery, and the ever-increasing development velocity. Too often, these mean a greater effort on the developers' side.
Under such conditions, it’s no wonder some corners are rounded, if not cut altogether. With a widening gap between C-suite goals, developers, and security teams, application security is often an afterthought in the application delivery chain.
However, priorities are shifting: 52% of organizations planned to increase their IT spending in 2023 and focus on cybersecurity. By 2025, the spending could reach $1.75 trillion cumulatively.
The even better news is that with proper security testing in place, you don’t have to slow down delivery.
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are the two most common testing technologies in the CI/CD pipeline to keep rogue code and vulnerabilities out of applications.
In this article, we’ll review and compare SAST vs. DAST tools. Spoiler alert—after reading this post, you likely won’t have to choose between DAST and SAST.
What Is Static Application Security Testing (SAST)?
Static application security testing (SAST) is a white-box automated testing technique to scan and analyze application source code and related dependencies (frameworks and libraries) for various security vulnerabilities.
These vulnerabilities include (but are not limited to):
- XSS-based attacks
- SQL injections
- Buffer overflows
- Keys and passwords embedded in the source code
- XML external entity (XXE) attacks
- OWASP Top 10 vulnerabilities
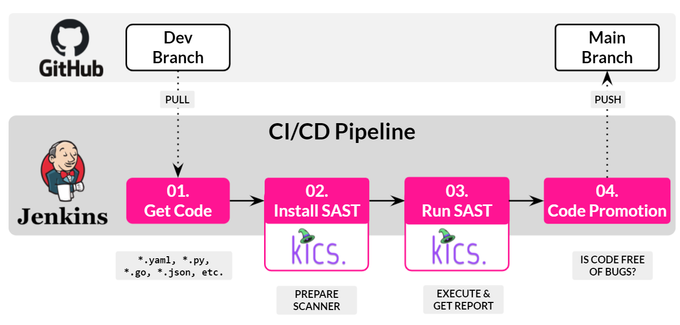
SAST tools are automated and set to run early in the CI/CD pipeline.
They are executed whenever code is committed to a source code repository (usually Git). SAST provides immediate and clear insights into potential vulnerabilities that may have been introduced into the code during the development process.
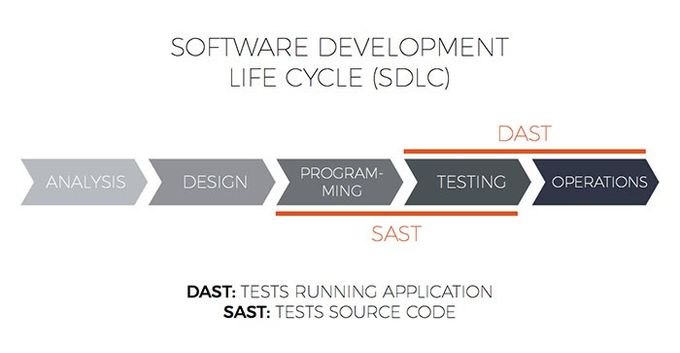
SAST is employed early in the SDLC to detect vulnerabilities and coding errors before applications are compiled. As such, it is one of the most widely adopted testing methodologies in development teams' shifting left security and implementation of the DevSecOps principles.
SAST Pros
- No need to run the application: Run SAST on your code and check for vulnerabilities without building or even having a fully functional app.
- Instant feedback: SAST tools quickly scan and analyze your code, providing near-real-time input and insights into the detected flaws.
- Easy integration: Most SAST scanners integrate seamlessly with popular CI/CD tools.
- Automatic execution: SAST runs automatically against reliable and accurate vulnerability databases—without interrupting or slowing developer workflows.
- Find early, fix early: Since SAST is performed early in the SSDLC —as early as pre-commit—it enables the developers to apply fixes before the code is compiled and shipped, and proactively mitigate security vulnerabilities and misconfigurations.
SAST Cons
- Low-hanging fruit: SAST uses predefined security rules to find publicly known vulnerabilities, so it is not as effective against business logic and runtime vulnerabilities, dynamic dependencies, supply chain attacks, and third-party service misconfigurations.
- False positives: SAST tends to produce many false positives. In a kind of “The SAST that cried CVE” situation, developers release vulnerable applications because they treat most issues as false positives—and they usually are. Until they aren’t.
Common SAST tools
The three most common tools for SAST are:
- Bandit: A tool designed to find common security issues in Python code.
- OWASP ASST: An open-source, source code scanning OWASP SAST tool.
- Semgrep: A lightweight polyglot static analysis tool that finds bug variants with patterns that look like source code.
What Is Dynamic Application Security Testing (DAST)?
To make it really simple, Dynamic application security testing (DAST) is the opposite of SAST.
DAST is a black-box technique for testing the behavior of running applications from the attacker's point of view.
Also called behavioral testing or “fuzzing,” DAST tools can help developers discover potential vulnerabilities to malicious attacks beyond the source code.
DAST tools scan more of an application's cyber attack surface, including API endpoints, web services, and elements of the application's cloud infrastructure or host system that may be compromised.
Implemented later in the CI/CD pipeline build phase, DAST requires some interaction from the tester to preconfigure testing parameters before the tests can be executed automatically.
These tools test the application against vulnerability sources like the OWASP Top 10 or SANS/CWE 25 to uncover runtime vulnerabilities before the application is pushed to production.
DAST Pros
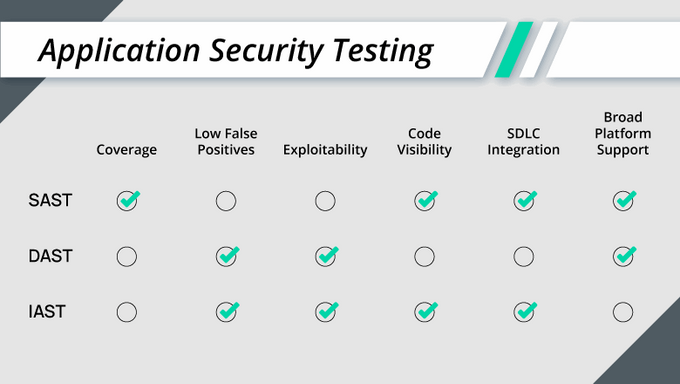
- Lower rate of false positives: With DAST implemented later in the build phase, the testing is conducted against the actual application and its runtime environment, so it catches actual (rather than potential) vulnerabilities.
- Polyglot by design: DAST does not require the tester to be familiar with the programming languages used in developing the app.
- No access to the code: There is also no need for accessing the app's code. DAST tools work transparently with any framework, making DAST a more robust testing methodology than SAST.
- Applicable to a broader area of the application’s attack surface: While SAST is limited to your codebase and dependencies, DAST can scan your IT infrastructure for misconfigurations, test API or web services, and run different attack scenarios.
DAST Cons
- Cannot point to the exact source of the vulnerability in the code: DAST scanners cannot access the application’s code, so they can't point developers to the specific section or line in the code causing the potential vulnerability. Dynamic application scan requires more manual work to pinpoint and resolve detected issues.
- Attack surface blind spots: Tools scan for a wide range of vulnerabilities within the application code but fail to seek out potential vulnerabilities in parts of the application stack that are not executed.
- Time and resource-consuming: Traditionally, DAST requires a specific skill set to configure and execute effectively. In terms of CI/CD minutes and waiting for an app to pass the tests, the time it takes to run DAST scans can be significant; complex applications and testing scripts can even take several days.
Common DAST tools
The most common tools for DAST are:
- OWASP ZAP by OWASP: The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools, actively maintained by a dedicated international team of volunteers.
- OSV-scanner by Google: Finds existing vulnerabilities affecting your project’s dependencies using the data provided by osv.dev.
- Legitify by Legit Labs: Detects and remediates misconfigurations and security risks across all your GitHub and GitLab assets.
SAST vs. DAST: Which Should You Use?
If you’ve read this far, you probably understood the spoiler in the introduction.
To build a robust and scalable application security testing strategy, you must employ both SAST and DAST in your pipeline.
It’s not really a question of which you should employ, but rather the question of when you should use DAST and SAST in your SDLC.
In fact, you’ll probably need SCA (software composition analysis) and IAST (interactive application security testing), depending on your application type, life stage, and its intended end-users.
» Learn about all the app security tools in Minimum Viable Security bundle.
SAST/DAST for Orchestrated Application Security Testing
Some of the main challenges with SAST and DAST are configuring and maintaining them as your application and potential vulnerabilities scale and grow.
Jit integrates with powerful DAST and SAST tools, some of which are mentioned in this article: Semgrep, Bandit, Legitify, OWASP ZAP, and OVS-scanner. The goal is to streamline and deliver a complete DevSecOps toolchain across IDE-Code-Pipeline-Cloud and Runtime.
With Jit, you get a complete Minimal Viable Security package that covers precisely what you need and doesn't waste resources on things you don’t.