Top 8 Git Secrets Scanners in 2026
Updated June 9, 2025

AI Summary
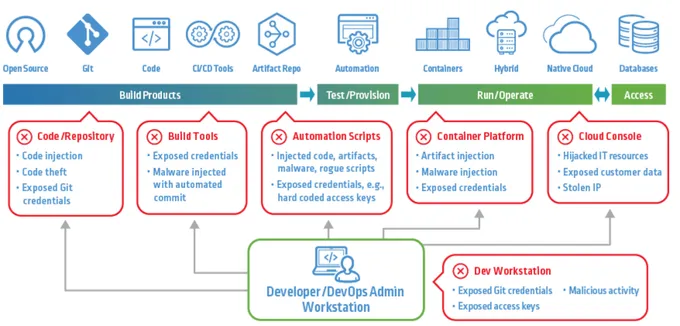
Leaked git secrets have become the proverbial kingdom keys for malicious actors seeking unauthorized access to a company's systems. And they are spreading fast.
The number of detected hard-coded secrets went up 67% from 2021 to 2022, and a staggering 10 million new secrets were found solely within public commits on GitHub. One small mistake in your source code may cause entire supply chain attacks that affect you and your customers irreversibly.
In the face of these growing threats, the need for practical secret scanning tools has never been more apparent. Fortunately, a wide range of git secret scanners can help safeguard your organization's secrets from falling into the wrong hands.
Top 8 Git Secrets Scanners in 2026 at a Glance
- Best overall Git secrets scanner in 2026: Jit
- Best tool for open-source Git history scanning: Gitleaks
- Best tool for enterprise-wide monitoring: GitGuardian
- Best Git secrets scanner for combined security testing: HawkScan
- Best tool for AWS-focused development: AWS Git Secrets Scanner
- Best Git secrets scanner for AI-enhanced detection: Spectral
- Best Git secrets scanner for high-entropy detection: Trufflehog
- Best tool for GitHub-native integration: GitHub Secret Scanning
What Is Secret Scanning?
Secret scanning analyzes code repositories to detect exposed sensitive data like API keys, credentials, or passwords embedded in your code, which malicious actors could use to initiate data breaches and unauthorized system access. Beyond individual data protection – secret scanning is about shifting security left to catch vulnerabilities before they reach production, while aligning with growing regulatory demands.
With the right git secrets scanner, you can proactively prevent exposed secrets from getting into the wrong hands.
Key Features for Git Secrets Scanners
Pattern-Based & ML Detection Combines high-precision regexes for well-known credential formats—such as AWS Access Key IDs (AKIA…) or GitHub Personal Access Tokens (ghp_…)—with machine-learning and NLP models that analyze entropy, structure, and contextual cues. This hybrid engine shrinks false-positive rates while still catching novel secret patterns that rigid regex alone would miss; critical for fast, noise-free CI pipelines.
Custom Rules & Secret Types Allows security teams to define org-specific patterns (e.g., internal API keys & database DSNs) in YAML or policy-as-code files. These custom signatures are version-controlled alongside source code, ensuring that new secret formats or compliance mandates can be enforced instantly across every repository and GitOps workflow.
Historical & Pre-commit Scanning Scans the entire Git history (--all refs) to surface legacy credentials and hooks into pre-commit or Husky scripts to block leaks before they reach origin. This dual approach protects both newly written code and long-forgotten commits, eliminating backdoor exposure when forks or mirror repos are made public.
CI/CD & Git Provider Integration Ships native actions for GitHub, GitLab CI jobs, Bitbucket Pipes, and Azure DevOps tasks that run secrets checks on every pull request or merge pipeline. Failed scans set required status checks, enforcing zero-secret policies automatically without manual gatekeeping and maintaining clean GitOps deploy workflows.
Remediation Guidance & Secret Revocation Outputs fix instructions that map each finding to its storage backend—suggesting git filter-repo commands, opening automated PRs with secret redaction, or triggering rotations through AWS Secrets Manager, HashiCorp Vault, or Doppler via webhook. Immediate revocation or rotation minimizes breach windows and aligns with platform security playbooks.
Top 8 Git Secrets Scanners in 2026
Benefits of Git Secrets Scanners
Git secrets scanning tools are essential for securing the development lifecycle by proactively identifying and neutralizing potential threats from exposed secrets. Here's how they help:
- Proactive threat neutralization: These tools effectively seal off avenues that could lead to data breaches or unauthorized system intrusions by finding and addressing exposed secrets before they can be exploited.
- Enhanced secure-by-design infrastructure: Incorporating Git secrets scanning directly into CI/CD pipelines bolsters a secure-by-design approach, integrating security seamlessly into your development process.
- Real-time vulnerability resolution: They provide real-time insights into security vulnerabilities, enabling rapid resolutions that perfectly complement agile development cycles and maintain high developer efficiency.
- Reduced remediation time and cost: By catching exposed secrets earlier in the software development lifecycle (SDLC), these tools prevent the much longer and more costly process of identifying and remediating issues in production, which would involve tracking down developers and disrupting workflows.
Keep Your Git Secrets a Secret
Git secrets scanners serve as a frontline defense to detect and eliminate hard-coded git secrets and vulnerabilities before malicious actors can exploit them. With the threat landscape in constant flux, your organization must prioritize integrating such tools to bolster its cybersecurity posture.
Jit makes security straightforward for development teams of all sizes, consolidating crucial security knowledge and providing a seamless tool integration layer that includes secret scanning. Explore Jit to unify git secrets scanners alongside SAST, SCA, IaC scanning, cloud misconfiguration scanning, and other tools for a single price – and ensure your secrets remain just that…secret.