5 Best Open Source Application Security Tools in 2026
Empowering developers with top-tier open source security tools for robust application protection
Updated November 26, 2024

AI Summary
As cybersecurity becomes increasingly important in software development, the “shift left” security approach is widely recognized as a best practice for ensuring superior application security. Numerous traditional security firms are introducing shift-left products and capabilities, and the concept is gaining traction.
However, some open source application security tools are more developer-friendly than others. That’s why we’ve compiled a list of five security tools that we believe developers should be aware of, providing a brief overview of the top open-source software and explaining why we consider them to be developer-friendly.
The list aims to cover various families of code analysis tools that should be part of some minimal requirements for security:
- Static application security testing (SAST)
- Dynamic application security testing (DAST)
- Hard-coded Secrets detection
- Infrastructure as Code analysis (IaC)
» Confused? Discover the differences between SAST and DAST
What Is Open Source Software?
Open source software is free, so there is no need for budget approval, allowing you to try out a tool without having to commit to it.
Instead of lengthy selection processes, you can simply try it and see how you like it. In addition, and it is particularly critical for security tools, they let you read the entire source code so that you don't have any surprises regarding what actions the tool is performing when running it in your environment.
Our Top 5 Picks for the Best Open Source Application Security Tools
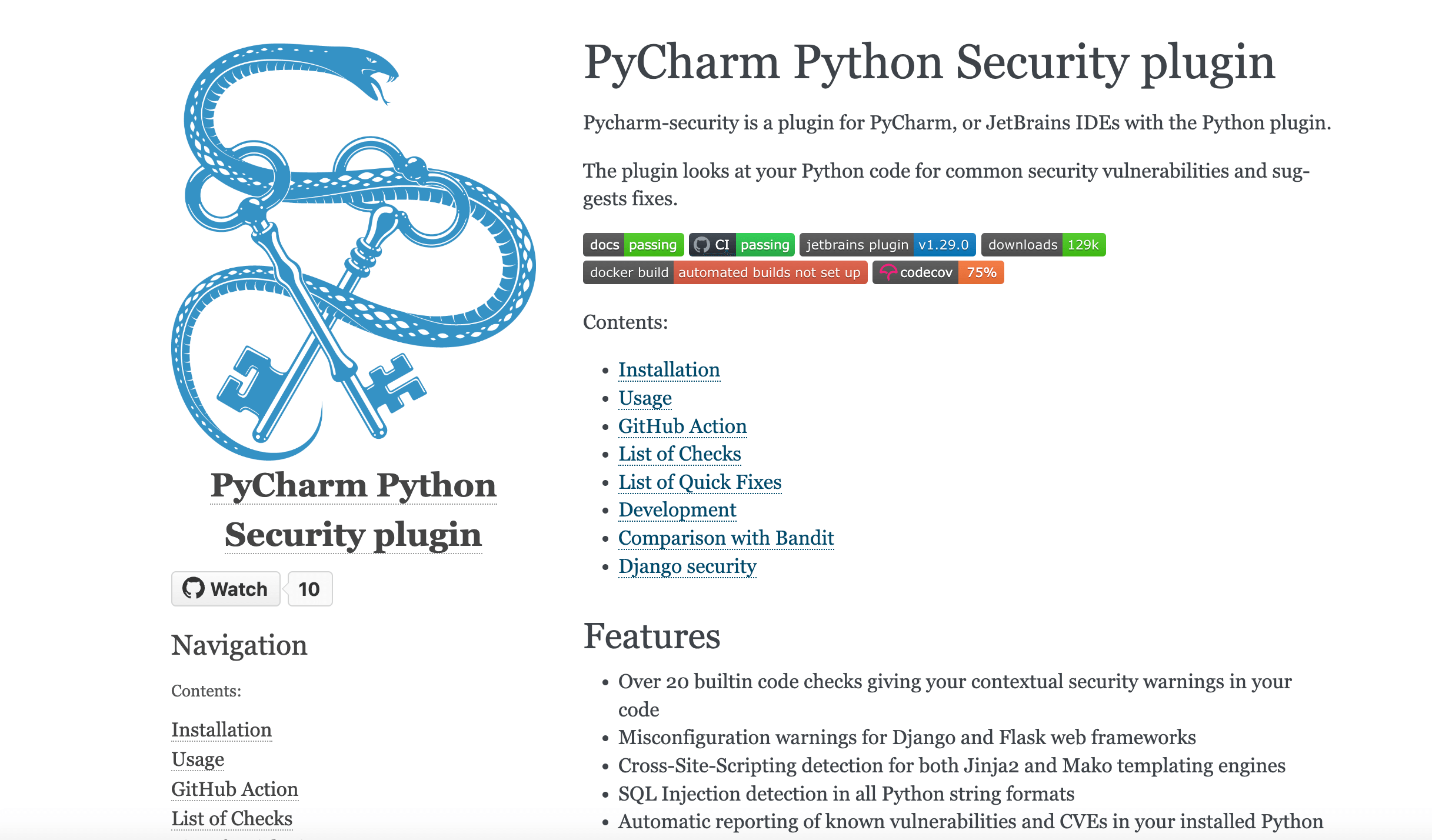
1. Best SAST tool for Python: Pycharm Python Security Scanner
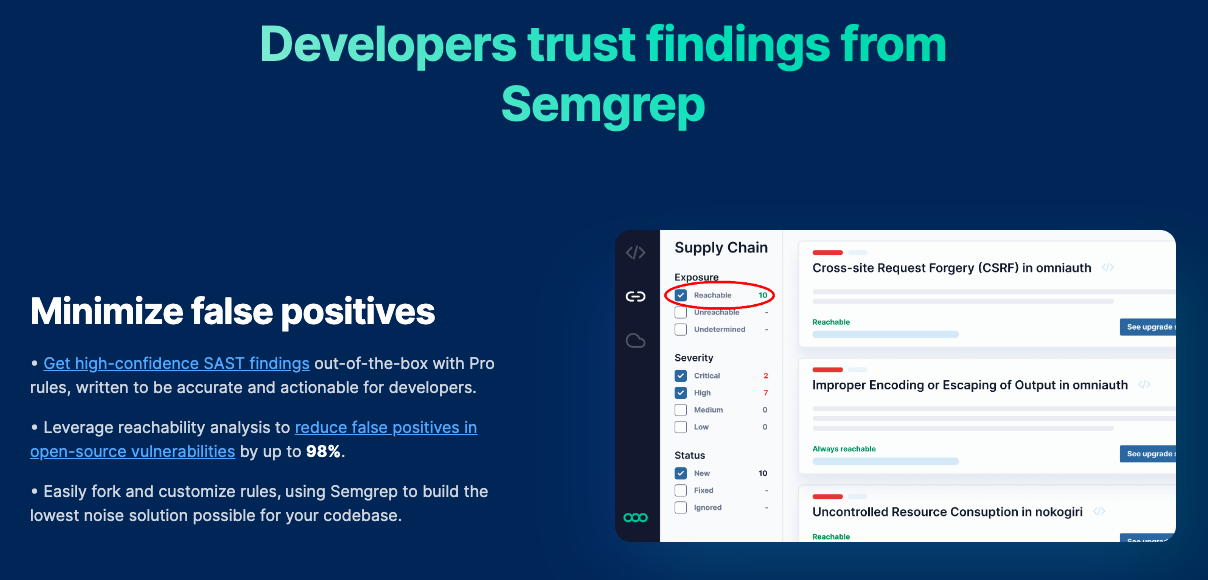
2. Most configurable SAST tool: Semgrep
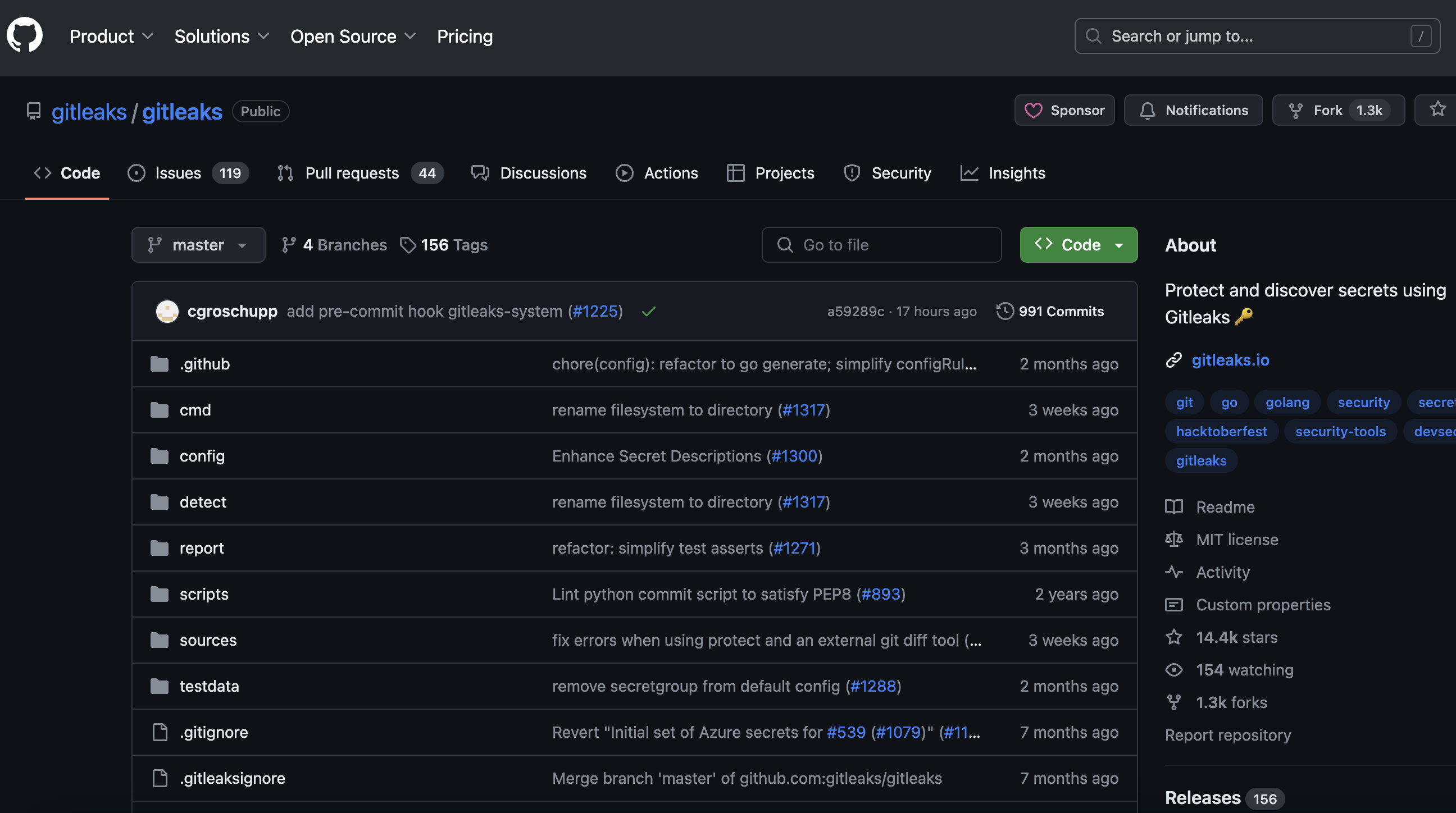
3. Best for finding secret leaks in code repositories: gitleaks
4. Best web vulnerability scanner: Zed Attack Proxy (ZAP)
5. Best IaC security scanner: KICS
A closer look at the criteria for open source application security tools
To us, a dev-friendly open source application security tool makes developers' (and dev leaders') lives easier by either making tasks simpler or speeding up processes.
1. They Run Locally First
Running code locally from your terminal allows software developers to launch and test code with one simple command. The ability to run a tool locally ensures that you can get immediate feedback and easily tweak the configuration. When launched from a container, you don't even have to bother with possible environmental issues related to compilation.
2. They Integrate With the CI/CD Pipeline
Open source application security tools that can be integrated into the CI/CD security pipeline have a higher value. We believe that once a tool has been used locally and has its usefulness verified, we'd like to run it continuously as part of the development lifecycle—and not only on our local machines using up local resources.
Of course, once a tool and process is part of the pipeline, the benefits are also extended across the entire dev team and codebase.
3. They Form Part of the Developer Work Environment
Developers should not be wasting time switching between development tools and security tools. All the tools on this list either run in the CI/CD pipeline (e.g. Github Actions) or as a plugin into the IDE.
4. They Have Great Documentation
Readily available documentation made for dev professionals can make or break smooth usage. With great “how-to” documentation, ramp-up and troubleshoot time is much shorter.
5. They Allow You to Configure the Output Format
If you can output the results of a certain tool in multiple formats, you then allow yourself to pipe results into another tool through an API or other form of integration. If results are only readable by humans, what you can then do with those results is limited and requires human effort and wasted time.
Adopting a “Born Left” Over “Shift Left” Approach
The industry is beginning to understand that merely “shifting left” is insufficient in a world of continuous delivery. We understand that today’s shift left open sources are not alleviating the overhead placed on developers due to the noise created and the burden of learning security and navigating each open source application security tool. It’s our responsibility to address this issue.
High-speed, forward-thinking development teams are adopting a new “born left” security strategy. In this approach, security considerations—like many other product aspects—are addressed right from the first line of code. Application security is not just delivered by the development team; it is owned by them.
» Learn more: Born left vs. shift left security
High-Velocity Development and Security
At Jit, our mission is to provide developers with an end-to-end solution for owning application security, from planning, through open-source orchestration, following an MVS approach (minimum viable security).
» See our solutions to build a modern minimum viable secure product
Development teams are being tasked with end-to-end responsibility and ownership of their products, while all along, there’s the pressure to ship code to production with high velocity.
As mentioned above, while dev-friendly security tools offer great benefits, the growing responsibility assigned to developers requires a shift in today’s approach—one that requires a minimum viable mindset and automated orchestration, so that devs will be able to own application security without compromising on velocity.