Cloud Security Controls: A Definitive Guide
Published September 6, 2025

AI Summary
The cloud undoubtedly delivered on its promise of agility. But it also left teams juggling siloed controls, rapid changes, and fragmented risk. When pushing code on demand and spinning up resources across AWS, GCP, Azure, and Kubernetes, it’s easy to lose track of what’s exposed, misconfigured, or missing a baseline defense against threats.
82% of enterprises report security incidents tied to cloud misconfigurations, most tracing back to gaps in day-to-day controls rather than exotic zero-days. This shows how agility without strong, embedded controls is a liability.
Controls are how organisations scale trust into their cloud pipelines: they enforce consistency, reduce the attack surface, and give teams a way to prove resilience without slowing delivery. Without them, every new deployment is a coin flip on whether the next incident is already in motion.
What Are Cloud Security Controls?
Cloud security controls are the tools, settings, and processes you implement to keep your cloud environments safe. They help protect your infrastructure, workloads, and data from common risks, such as misconfigurations, breaches, or policy drift.
At their core, controls define how infrastructure, applications, identities, and data are expected to behave and enforce those expectations in real time. Strong controls continuously detect when environments drift from baseline and provide the context teams need to respond quickly and effectively.
There are three basic types of controls you should consider implementing:
Preventive controls stop insecure behavior before it can take root. For example, enforcing least privilege on IAM roles, applying IaC policies, or requiring branch protections in GitHub.
Detective controls focus on visibility, monitoring for violations, and drift through runtime misconfiguration detection, secret scanning, or anomaly alerts.
Corrective controls close the loop by fixing issues or guiding remediation, such as auto-remediation for Kubernetes workloads or GitHub Actions that roll back non-compliant changes.
You must apply those controls across several layers: identity, network, compute, data, application, and CI/CD pipelines. And you’re probably dealing with all that across more than one cloud provider, in a containerized or serverless setup, running IaC through GitOps. That’s why implementing cloud security controls is as much an orchestration challenge as a tooling one.
Standards and frameworks like CIS Controls, CIS Benchmarks, AWS FTR, or SOC 2 audits offer engineering teams a more precise definition of effective cloud security. They help validate that your implemented controls are operational and aligned with best practices. However, coordinating those controls so they stay relevant and enforced as your cloud environments evolve and workloads change is where many teams get stuck.
The 5 Core Categories of Cloud Security Controls
Like in traditional on-prem environments, securing the cloud isn’t a single-layer job. You’re dealing with overlapping surfaces from identity to infrastructure to application logic. Each needs its own class of controls to reduce security risk without slowing velocity.
1. Infrastructure Controls
Infrastructure controls govern how cloud resources are provisioned and secured. Key practices include enforcing hardened AMIs, ensuring S3 buckets are always encrypted, blocking overly permissive security groups, and preventing public IPs on sensitive workloads. The challenge is embedding checks to run consistently and provide visibility across AWS, GCP, and Azure environments. Tools such as Prowler and Kubescape can help, but the real goal is to codify these controls into pipelines so misconfigurations are caught before they reach production.
2. Application Controls
App-level controls are most closely tied to your developers' shipping. These include SAST, secrets detection, API security, SBOM generation, and web app scanning. If you’ve ever tried to get your team to fix a hardcoded secret before a release, or figure out whether a library has a high-severity CVE, you’ve felt the friction here. These tools are only practical when integrated into the pipeline, which is why orchestration is key.
3. Identity and Access Controls
These controls govern who can do what (and whether they’re doing too much). Strong IAM controls include least-privilege permissions, role-based access, and mandatory multi-factor authentication. In practice, however, teams often accumulate stale access keys, IAM roles with wildcard privileges, or secrets shared outside secure vaults. These gaps rarely trigger obvious errors but quietly expand the attack surface.
4. Pipeline and DevOps Controls
Pipeline and DevOps controls safeguard the software delivery process itself. They are checks built into CI/CD workflows to ensure only secure, approved code makes it into production. Typical examples include branch protection rules, dependency and secret scanning, mandatory peer reviews, signed build artifacts, and automated tests or policies that must pass before a merge or deployment. These controls aim to catch insecure changes at the source inside the tools engineers already use, so you can identify and address risks before they are released.
5. Data and Network Controls
These controls focus on where your most valuable assets live and move. That includes encryption in transit and at rest, access controls on databases and storage, firewall rules, VPC segmentation, and rate limiting on exposed APIs. For example, if a database snapshot is publicly accessible or a VPC is misrouted to the internet, these controls should catch it. This layer often lacks visibility or cross-team ownership.
Why You Must Have Strong Cloud Security Controls In Place
Cloud-native development has outpaced legacy security thinking. Infrastructure changes by the hour, and ephemeral workloads come and go. Also, engineers now push directly to production multiple times a day. That agility means traditional perimeter models and static checklists are no longer enough.
In 2025, misconfigurations, overly permissive IAM, and drift between code and cloud are consistently among the top drivers of cloud breaches. You see this in every cloud incident post-mortem: a default setting left unchanged, a secret committed and forgotten. These risks now multiply faster in multi-cloud environments where every provider has its own IAM quirks and configuration surfaces.
Regulatory audits won’t wait for security to catch up with velocity. Compliance with SOC 2, ISO 27001, and GDPR requires proof that controls are defined and enforced continuously. If those controls are scattered across spreadsheets, static documents, and ad hoc scripts, teams also increase exposure and risk failing audits.
Pulling these layers together helps your team develop and maintain a cyber resilience strategy that keeps systems running even when gaps or breaches occur.
7 Best Practices for Maintaining Strong Cloud Security Controls
1. Architect for Security from Day One
Modern cloud environments built on containers, serverless, and IaC are too dynamic for security to be bolted on later. The foundation must be secure by default, with controls embedded into technical and cultural architecture.
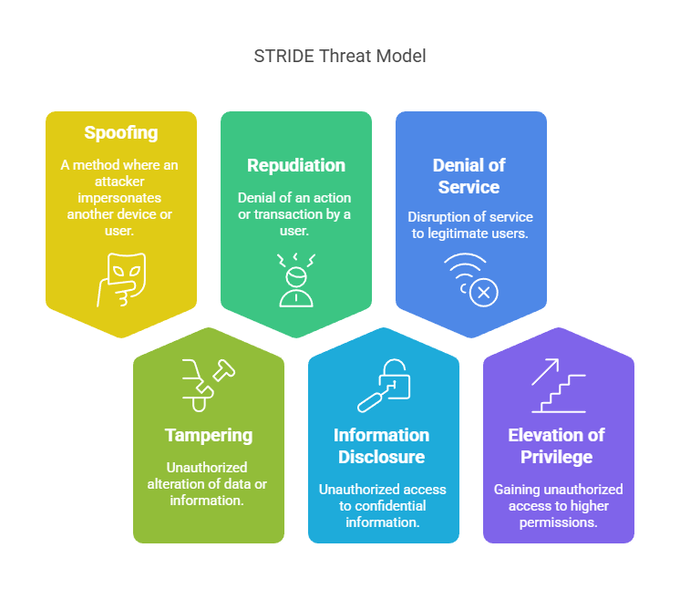
The best way to achieve this is to use threat modeling early in design phases. Lightweight models like the STRIDE threat model, attack trees, or OWASP’s Cloud Top 10 can highlight where authentication, authorization, and logging controls must be enforced.
In practice, this means enforcing least privilege across every layer. For example, IAM roles should begin with deny-all and be granted only the exact permissions required for each service. To make these safeguards repeatable, embed them as secure defaults in IaC modules and repository templates so that every new workload inherits the correct posture. Build Terraform modules that enable TLS and encryption automatically, add audit logging by default, and enforce MFA across services.
2. Enforce Controls as Code
Controls can’t live in shared folders. The best way to scale security without slowing your developers is to codify controls in the same systems they already use. Treating security policies as code also gives teams the same benefits as other engineering artifacts: peer review, auditability, and continuous validation.
Define policies in YAML, JSON, or OPA/Rego and keep them under version control alongside application and IaC code. IaC linting rules, dependency scanning, and CI/CD guardrails should all run automatically in pull requests, blocking merges when they fail.
Jit operationalizes this by codifying security best practices into Security Plans as Code. These plans embed directly into GitHub or GitLab workflows, enabling consistent rollout of controls across code, infrastructure, identity, and runtime. You get tools like SAST, SCA, IaC scanning, DAST, and CSPM activated through plan configuration files, so your policies are executable and enforceable within the systems developers already use.
3. Detect and Manage Drift Continuously
Cloud environments inevitably drift. Resources change, new services are spun up, and security posture can silently erode over time. Most teams notice drift after an incident, but building a feedback loop from runtime to repo avoids this.
Use CSPM tools or IaC scanners to evaluate live cloud resources against your declared configurations continuously. For example, detect if a storage bucket is exposed to the public when your Terraform module specifies private access. When drift occurs, surface it directly in developer workflows: auto-create GitHub issues or pull requests that propose a fix back to the IaC baseline.
Over time, this loop turns runtime corrections into durable, version-controlled improvements - essentially a preventative maintenance program for your cloud environment that ensures posture doesn’t silently degrade between audits.
4. Prioritize by Threat Over Compliance
Compliance frameworks like SOC 2, ISO 27001, and PCI are essential, but don’t map one-to-one with real attacker behavior. Many breaches happen through gaps that technically weren’t non-compliant but were trivial to exploit. Security teams that measure only against checklists end up fixing the wrong things first.
The stronger approach is to prioritize based on exploitable risk. That means evaluating findings in context: is the asset internet-exposed, connected to production data, or running in a privileged role?
Tools that understand exposure (public endpoints, sensitive identities, unencrypted data) help focus engineering attention where it matters. Weight vulnerabilities by asset criticality, not just severity score, and tune alerting so high-risk exposures rise to the top of triage. A compliance report might say “pass,” but a context-driven risk model tells you where an attacker could get in tomorrow.
5. Automate Remediation Workflows
Finding issues is easy; fixing them at scale is where most teams fail. Backlogs grow unmanageable, developers disengage, and high-risk misconfigurations linger in production.
Remediation needs to be automated and contextual. Create actionable tickets in developer systems like GitHub, Jira, or Linear with clear descriptions of what failed, where, and why it matters. For IaC drift, auto-generated pull requests should propose compliant configuration changes. For runtime violations, automated playbooks or admission controllers can correct the issue directly while keeping teams informed.
Jit addresses this gap through its AI Agents and Context Engine. Findings are triaged and prioritized by runtime risk; for example, highlighting an exposed production-facing endpoint ahead of a low-impact misconfig. To avoid flooding teams with duplicate alerts, Jit consolidates and de-duplicates issues, giving your engineers one-click remediation plans directly where they work. The result is a remediation process that scales with development speed and reduces risk without overwhelming teams.
6. Extend Controls Beyond CI to Runtime
Pre-deployment checks can’t account for everything. Once code runs in production, new risks emerge, such as container escape attempts, ephemeral secrets lingering too long, or IAM tokens reused across namespaces. Controls must extend beyond the CI/CD stage to monitor workloads in motion.
Runtime controls include network segmentation at the cluster level, workload behavior monitoring (such as spotting privilege escalations in pods), and active scanning of public surfaces like APIs and domains. Instrument logging and anomaly detection flag deviations like unusual outbound traffic immediately.
7. Centralize Visibility and Posture
Most organizations quickly accumulate a large number of security tools. Without centralization, this creates a fractured view of posture, where no single team can confidently answer the real risks or know who is fixing them.
A central visibility layer should consolidate findings across code, pipelines, and runtime, and correlate them to their impact. Instead of a raw list of “misconfigured roles,” teams must see which ones expose sensitive data stores or production services. Visibility also requires clear accountability: every issue must be tied to the repository, service, or team that owns it. In most organizations, this oversight sits with the CISO or vCISO, who enforces ownership and encourages teams to improve their security posture.
Baking Security into Cloud-Native Development
Between containers, ephemeral infrastructure, CI/CD pipelines, and multiple cloud accounts, the only sustainable approach is operationalizing the proper controls at the right time. You need orchestration, automation, and code-native enforcement that fits directly into how your team builds and ships.
Jit turns product security into something your engineers can actually act on. Through Security Plans as Code, teams can align with baselines like MVS, SOC 2, or ASVS and activate the proper controls directly within GitHub and GitLab. Jit’s AI Agents and Context Engine extend this foundation by turning fragmented alerts into prioritized, contextual insights. AI Agents automate risk triage, compliance mapping, and remediation ticketing tasks, while the Context Engine enriches findings with runtime, ownership, and business impact.
The result is a unified platform that enforces controls, highlights what truly matters, and routes fixes into developer workflows. With it, teams can resolve issues quickly, at scale, and without leaving the tools they already use. Get your Jit demo here.