A Guide to Running Secret Scans for Free with GitLeaks and Jit
Updated November 26, 2024

AI Summary
The world is safer when secrets remain secrets. The same sensitive information that is meant to keep your systems safe is an increasingly common source of cyber attacks. And the number of leaked secrets just keeps on growing.
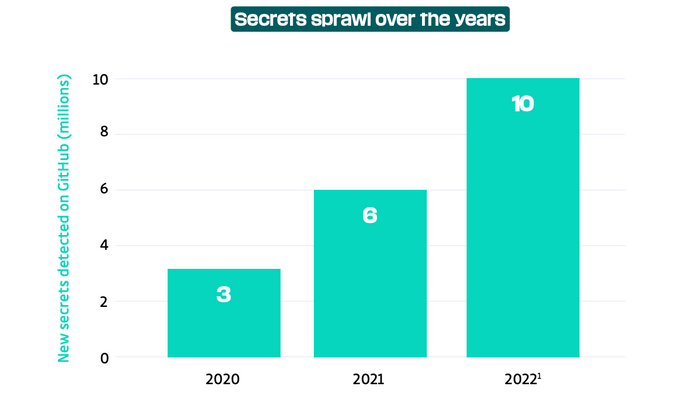
Of the 13.3 million users who pushed code to GitHub in 2022, 1.35 million have accidentally exposed secrets. Each of these exposed secrets poses a serious threat, from user impersonation to leaked credentials or data and money theft.
Proper secret scans are paramount to safeguard sensitive information, ensure data integrity, and prevent attackers from running rampant through your system. But you need to know where your secrets are before you can manage them.
What are secret scans, and why do you need them?
Secret scans detect sensitive information within a codebase, such as passwords, API keys, SSH Keys, tokens, or private credentials. They scan through code repositories, including past commits and all branches, to identify and flag secrets that can lead to unauthorized access or accidental data exposure.
The adoption of these tools has become increasingly vital due to the escalating number of cyber attacks and the inherent vulnerabilities in modern, collaborative software development processes. Automated secret scans are crucial in maintaining a secure-by-design infrastructure, where data protection is safeguarded from the first stage of the SDLC.
Running secret scanning tools brings several vital benefits:
- Enhanced Security: they offer a critical layer of protection against the accidental exposure of secrets at the early stages of the SDLC. This helps you shift security left and improve agility in code development.
Customization: Beyond detecting general patterns, you can tailor these tools to recognize specific patterns unique to an organization, offering a more personalized security approach.
Scalability: As organizations grow and their codebases expand, these tools can scale accordingly across repos, ensuring consistent secret scanning coverage.
Reporting and Analytics: Many secret scanning solutions provide detailed reports and analytics to measure detected secrets and resolved security risks over time.
- Regulatory Compliance: Secret scanning helps organizations comply with critical regulations like HIPAA and GDPR by safeguarding sensitive information. Compliance is particularly vital in industries like healthcare and finance, where data protection is tightly regulated.
Key challenges of secrets scanning across repos
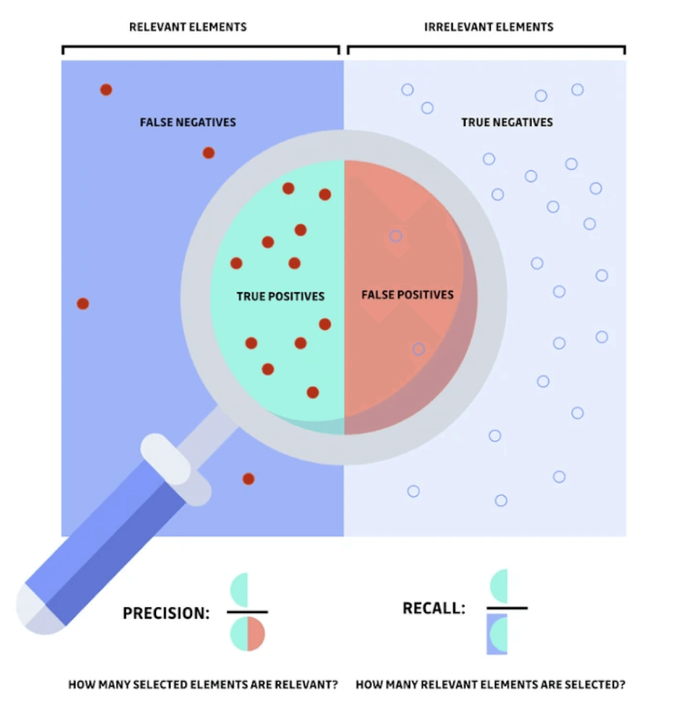
1. False Positives
It’s imperative to consider secret scanning accuracy in detecting false positives and negatives. 20% of alerts are false positives, sending developers on a wild goose chase that will only waste their time and efforts (with unnecessary added stress and fatigue).
2. Lack of Context
A lack of contextual understanding of vulnerabilities is often the cause for incorrect flagging, so make sure your tool goes deep into each vulnerability to ensure it poses a risk before alerting your team. Can the secrets scan determine whether secrets are actually reachable in production? What is the business context of the data the secret protects? Can it be exploited from the internet?
3. Dynamic and Encrypted Secrets
Dynamic secrets and regular credential changes make it challenging for scanning tools to correctly and consistently track vulnerabilities. Similarly, encrypted secrets may be missed by standard patterns. Ensure your tool leverages pattern recognition and cryptographic analysis techniques to identify encryption formats.
4. Legacy Codebases
Legacy codebases may contain outdated secrets that are no longer in use but could be harmful if exposed. Plus, they often depend on outdated third-party libraries that may have known vulnerabilities and inadvertently disclose sensitive information. Ensure you create an inventory of all repos containing legacy code so you can understand the architecture of your legacy systems.
5. Lack of Repo Coverage
Some secret scans may only examine some branches, potentially missing secrets not in the main code path. This lack of coverage could lead to severe supply chain risks and an inaccurate security posture assessment. Jit offers change-based security tests in pull requests to address this issue.
How to Run Secret Scans: Step-by-Step Guide
For this tutorial, we will conduct secret scans using Gitleaks and Jit.
Jit removes any headache from configuring and deploying Gitleaks. Simply sign up for free, connect Jit with your repos, and begin pushing code. Jit will automatically run Gitleaks against your code as you create new PRs – surfacing exposed secrets along the way.
1. Prerequisites for Secret Scans
Before you start, ensure you have a Jit account and the necessary permissions to access the repositories you wish to scan – connecting Jit with your GitHub account takes a matter of minutes (as you’re about to see). You should also have Git installed on your machine to clone repositories.
2. Installation
By default, Jit uses Gitleaks for secret scans, so you don't have to install Gitleaks when using Jit.
3. Integration with GitHub
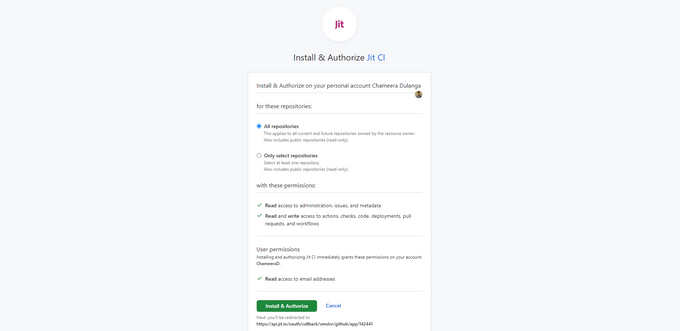
To get started, you need to connect your GitHub account to the Jit dashboard. You will see an option to Integrate GitGub in the Security Plans tab.
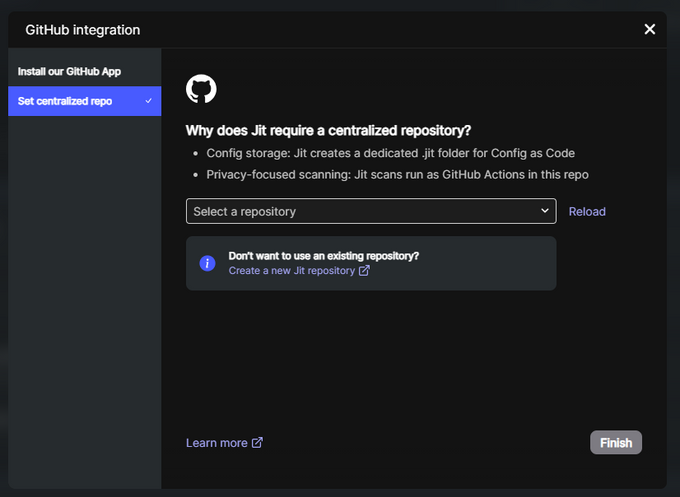
Then, it will open a model like the one below, which will take you through several steps to connect to your GitHub account and grant access to repositories.
Finally, create or select an existing GitHub repository as the centralized repository for Jit. It will be used to store configurations and run GitHub Actions.
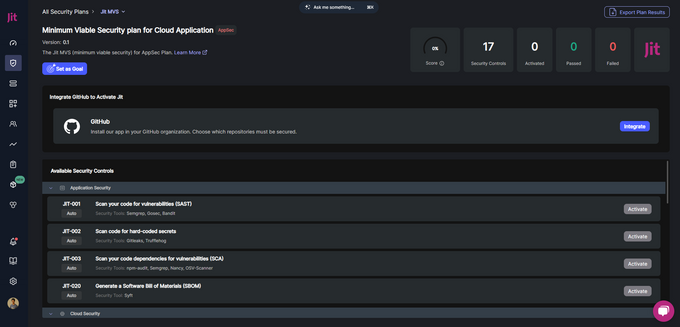
4. Running the Secrets Scan
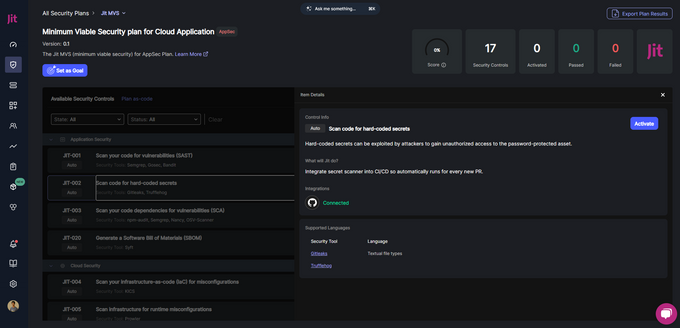
Then, you will see a list of 17 Jit security controls under four categories:
- Application Security
- Cloud Security
- Web Application Security
- CI/CD Security
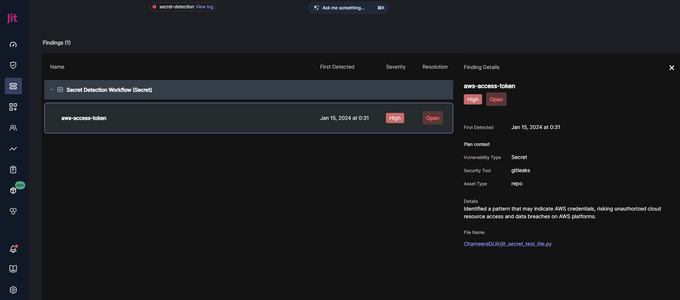
Select the Scan code for hard-coded secrets (JIT-002) option under Application Security to perform a secret scan using Gitleaks. Jit will integrate the scanner into your CI/CD pipelines to perform scans for every new PR.
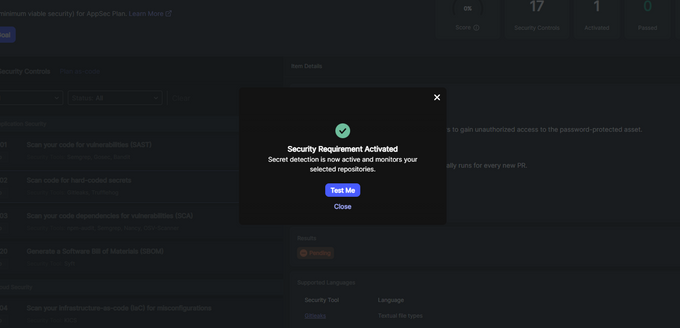
Click on the Activate button to enable this feature.
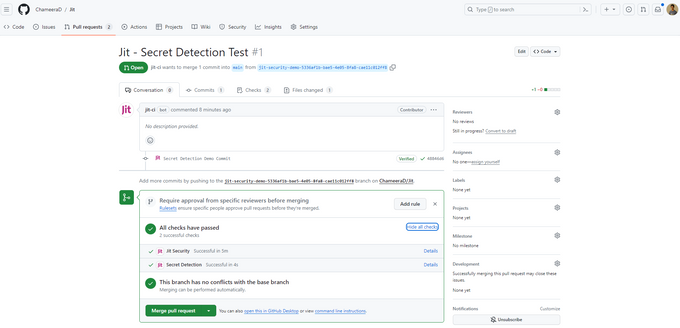
Now, when you make a pull request on the selected Git repositories, Jit will perform a secret scan through Gitleaks.
Jit only scans for vulnerabilities caused by newly introduced code, so the scan time is exceptionally fast. Exposed secrets are highlighted entirely within Github – from secrets scanning to remediation – so developers never need to leave the PR to find and fix security issues.
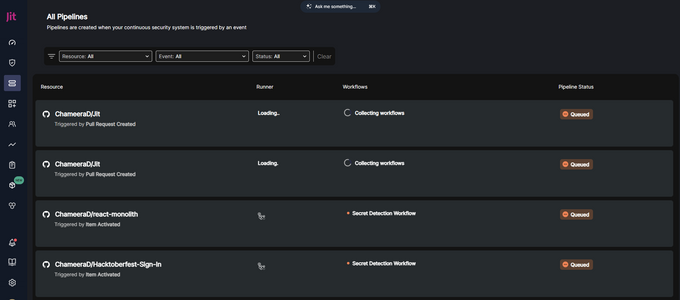
You can monitor all the pipelines from the Pipelines tab to confirm that Git is running scans across your repos in a centralized place.
In case of a failure, you will need more details. For that, click on the relevant pipeline from the Jit dashboard, which will take you to the results of the scan. This is an alternative to investigating the results of secret scans within GitHub, which is how most Jit users solve security issues.
5. Remediating Issues from a Secrets Scan
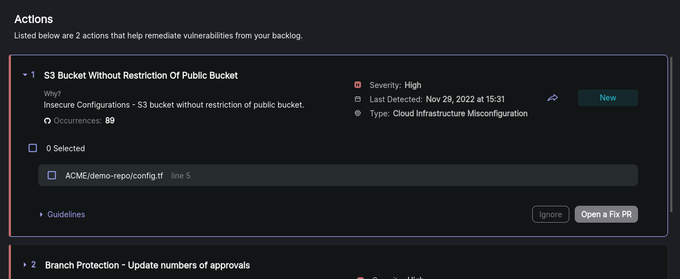
The Actions tab provides straightforward suggestions to address security concerns and misconfigurations in the Backlog – including exposed security issues from secret scanning. Each Action represents a collection of one or more related issues, allowing for grouped fixes through automated remediation. This aggregation simplifies the process of resolving common types of problems collectively.
6. Fixing an Issue
- Select and expand the Action.
Click the Fix (Open PR) button.
- Navigate to GitHub by clicking the View Fix PR button and merge the PR. Then, Jit will rerun the scan and verify if the issue has been addressed.
7. Ignoring an Issue
If there are issues that you can ignore, select the Ignore option after expanding the Action. Use Ignore to quickly dispose of false positives.
With this guide, you have all the steps to run secret scanning across your repos. Sign up for Jit to do it yourself for free!
Your Secrets are Safe with Jit and Gitleaks
Automating secret scans ensures a consistent, efficient, and thorough examination of your code for vulnerabilities, reducing the risk of security breaches. By running Gitleaks with Jit as part of the CI/CD process, developers can identify any secrets that have been committed in the past and proactively fix them.