8 Best Practices When Using AWS Security Groups
To ensure your AWS environment is safe and secure, it's essential to implement efficient AWS security groups.
Updated December 3, 2024

Are you concerned about the security of your AWS environment? With over 73% of businesses having at least one critical security misconfiguration, it's essential to take proactive measures to protect your data and applications. While AWS is responsible for the security of the underlying infrastructure, you are responsible for securing your data and applications in the cloud.
AWS Security Groups are a crucial component of your security architecture, but misconfigured security groups can lead to serious security breaches. In this article, we will explore eight best practices that can help you secure your AWS environment effectively.
AWS Security Groups Best Practices
1. Authorize only specific IAM principals and IP address ranges
2. Avoid using "default" security groups
3. Restrict inbound and outbound access
4. Simplify the management of security groups
5. Minimize the number of security groups
6. Delete all unused security groups
7. Avoid using large port ranges
8. Enable VPC flow logs on inter-VPC flows and internet flows
What are AWS Security Groups?
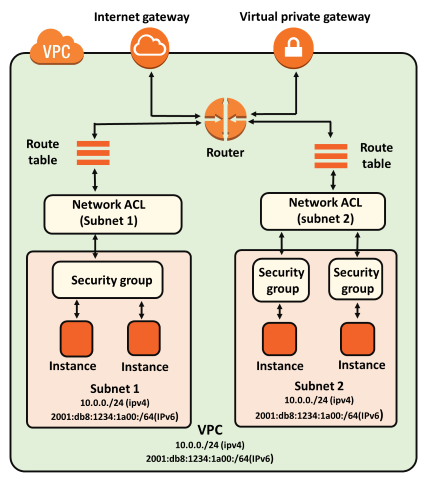
AWS security groups are tools used to manage network access to AWS resources. They act as a virtual firewall for your AWS account, controlling inbound and outbound traffic.
Security groups are made up of rules that define what traffic is allowed in or out of an AWS resource, fostering continuous security. When you create a new AWS resource, you can specify which security group it should belong to. You can also add and remove resources from security groups as needed.
» Get a checklist for bootstrapping a secure AWS as-Code environment
How do AWS Security Groups work?
AWS Security Groups are a virtual firewall for your AWS account. They allow you to control inbound and outbound traffic to and from your AWS resources (such as an EC2 instance or an RDS database). You can create multiple security groups for each VPC and add rules to each group based on your security needs. You can allow or deny traffic based on various criteria, such as IP addresses, port numbers, and protocols.
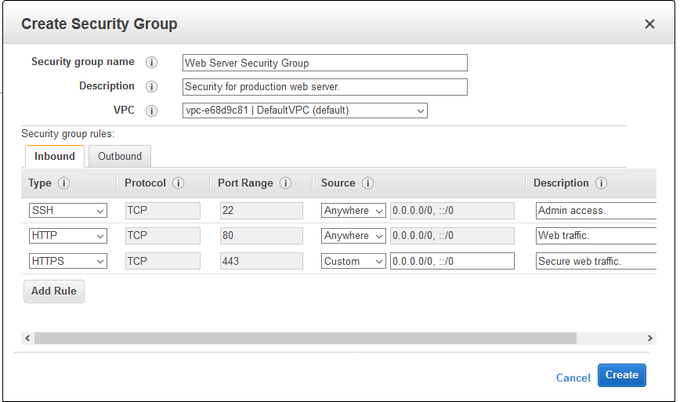
For example, you could create a security group for your web servers that allows inbound traffic on port 80 (for HTTP traffic) and port 443 (for HTTPS traffic). Similarly, you could create another security group for your database servers that allows inbound traffic on port 3306 (for MySQL traffic).
If you need to allow access to your AWS resources from new IP address ranges, you can add a rule to the security group for that resource. This flexibility enables you to keep your AWS resources, such as an EC2 instance or an RDS database, secure and accessible to authorized users.
» Learn the secrets of effective security orchestration
Which services need Security Groups?
All AWS services, especially EC2 instances, require security groups. Amazon EC2 is a highly popular service. In AWS's Shared Responsibility Model, both AWS and clients share security responsibilities. Despite AWS providing cloud protection, clients must manage their security group configurations.
» Save time with AWS Security Token Service
8 Best Practices When Using AWS Security Groups
AWS has over 200 services, making it challenging to navigate. However, by following best practices when using AWS security groups, you can simplify this complexity into a checklist guide. This will help your organization keep track of different security settings and options more comprehensively and predictably.
While open-source security tools exist to help mitigate problems, starting from the bottom up with AWS security rules can significantly reduce potential threats to your servers and services. Here are eight best practices when using AWS security groups.
1. Authorize only specific IAM principals and IP address ranges to access groups
To avoid unauthorized access to sensitive resources, it is important to restrict permissions to the IAM console. This can be achieved by authorizing only specific IAM principals and IP address ranges to access groups.
By doing so, only authorized users can modify access groups, and any unauthorized access attempts can be easily detected and blocked. If access to the IAM console is left unchecked, anyone with access to it could modify access groups and potentially grant themselves unauthorized access to these resources.
2. Avoid using "default" security groups
Default security groups have open inbound and outbound traffic, which can harm your account. Anyone with access to the default security group can access all of the resources in your account, which can be a security risk. To prevent this, you should create a new security group and add only the specific rules you need to manage your resources.
3. Restrict inbound and outbound access
Allowing all inbound access to some or all ports can make your network vulnerable to malicious attacks by unauthorized users. Therefore, by restricting inbound access, you can prevent unauthorized users from gaining access to the network.
Similarly, allowing all outbound access can enable any user on the network to send malicious data out to the internet. Therefore, restricting outbound access can help prevent users from sending out malicious data.
4. Simplify the management of security groups
You can simplify the management of security groups by adding a brief description to each security group rule. This way, you won't have to keep track of this information using spreadsheets or other easily misplaced documents.
Adding details such as the reason or date of creation for each rule lets you quickly find the necessary information within AWS VPC and AWS EC2-Classic security groups.
5. Minimize the number of security groups
To simplify auditing and managing errors, it is advisable to minimize the number of security groups. Having too many security groups can lead to excessive permissions and access to resources.
Therefore, it is important to use each security group to manage resources that have similar functions or security requirements. Doing so will make it easier to reduce the number of security groups and prevent errors.
6. Delete all unused security groups
Unused security groups can pose a serious security risk. If someone gains access to an unused group, they might be able to access resources that are not meant to be accessed by them. You can use the AWS console or the AWS CLI to delete unused groups.
7. Avoid using large port ranges
Allowing a large range of open ports increases the system's attack vulnerability. Attackers can target any open port within the range, making it more likely that they will find a way to gain access to the system.
To prevent this, it is recommended that security groups be configured with only the necessary ports. This way, if an attacker finds an open port, they will not be able to access any other parts of the system.
8. Enable VPC flow logs on inter-VPC flows and internet flows
Doing this can be helpful for debugging and troubleshooting communication and connectivity issues. By default, VPC flow logs do not capture traffic within the same VPC.
However, you can enable VPC flow logs on inter-VPC flows by creating a flow log that captures the desired traffic type. To enable VPC flow logs on internet flows, you can allow them on the internet gateway that is attached to your VPC.
» Explore the latest open-source product security tools
Continuous AWS Security for your DevOps
To secure your AWS environment, don't rely solely on security groups. Implement security measures throughout the CI/CD pipeline with tools like Jit, which integrates with other application security tools such as Gitleaks and OWASP ZAP. This helps create a comprehensive DevSecOps strategy, making it easier to embed security controls across the workflow.
Jit covers all layers of your cloud app, including code, CI/CD pipeline, cloud, APIs, and more, so you can be proactive in securing your application.