What is MTTD, and how can you crush it
Updated August 19, 2025

AI Summary
Seven months. That’s the average time it takes to detect a cyber threat, according to a recent IBM study. If this figure isn’t alarming enough, you can couple it with the millions of dollars that cyber-attacks cost businesses in damages and lost profits.
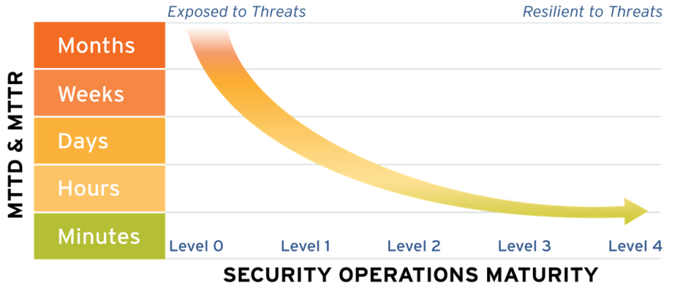
We all know the importance of speed in writing code and deploying applications, but what about speed in detecting security incidents? Knowing how fast your team can detect incidents is the only way you can have a clear picture of what is working and what isn’t and improve your Mean Time To Detect (MTTD).
But metrics are only useful if you actually work on improving them. So how can you improve your response time? In this article, we will dive into MTTD and provide practical steps that you can take to detect cyber threats faster and better protect your business.
What is Mean Time To Detect (MTTD)?
Mean time to detect (MTTD) is a basic performance indicator that measures the average time it takes for organizations to spot cybersecurity incidents. Calculating the MTTD is as simple as dividing the teams' time spent on incident detection by the number of incidents identified.
Companies use MTTD to evaluate the effectiveness of their security operations and identify areas for improvement. It indicates the effectiveness of the security controls and provides an intuitive method for testing new tools or processes. The benefits of lowering MTTD go way beyond reducing costs and avoiding attacks (though those could be enough reasons to measure and improve your MTTD). A low MTTD means that your team performs better, can detect and solve issues faster, and, subsequently, deliver high-quality software faster. That’s the goal of any DevOps team at the end of the day.
MTTD vs. MTTR: what are the differences?
MTTD and MTTR measure similar variables, but the devil is in the detail. MTTD focuses on the time taken to detect an incident. It indicates the effectiveness of an organization’s monitoring and detection mechanisms but doesn’t go beyond the detection step. In contrast, MTTR focuses solely on remediating an incident. It measures how fast your team can respond to/fix incidents once they are detected.
How can you calculate your MTTD?
Deriving the Mean Time To Detect (MTTD) is as easy as dividing the total time taken to detect security incidents within a given time by the number of detected incidents. To further simplify this process, we can use the following formulae:
Mean Time To Detect = Total Time Taken To Detect Incidents / Number of Incidents
Where: Total Time Taken To Detect Incidents = Incident 1 Detection Time + Incident 2 Detection Time + ...
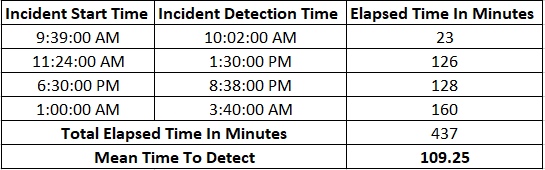
Here’s an example of MTTD calculations:
- Identify the start time of each incident detected
- Calculate the time elapsed from the start time to the detection time in minutes
- Calculate the total elapsed time for all the incidents recorded
- Divide the total elapsed time by the number of incidents recorded
7 Steps to help crush your MTTD
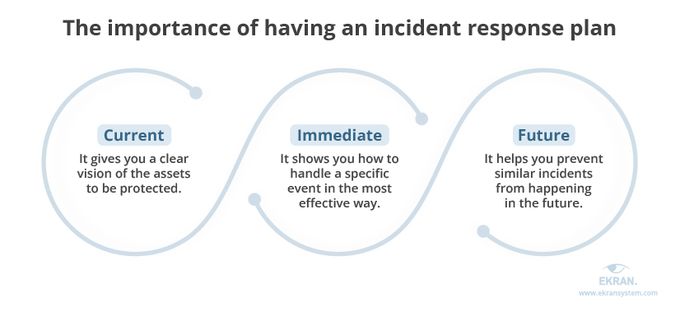
1. Create an incident response plan
You must develop a comprehensive incident response plan before a cybersecurity incident occurs. It ensures you have a plan to follow to conduct the incident response while identifying key stakeholders such as incident response team members and communication teams.
Your plan must consider the organization's resources and any strengths and weaknesses and cover all the entities within the organization to ensure its effectiveness. This stage also includes ensuring that the response teams have adequate awareness of the plan and training to act based on what was agreed upon.
2. Improve your observability
To stay ahead of the game, you need much more than monitoring. Typical monitoring involves collecting logs and analyzing them; however, it only gives you a partial understanding of the entire picture. Gaining complete visibility into the application and distributed systems must include observability that combines logs, traces, and metrics to provide in-depth analysis and visibility into any issue that may surface. For this, it’s worth looking into a Continuous Security Monitoring tool that automates security processes, gives you a birds-eye view over the entire application, and makes it easier to detect vulnerabilities and respond to them in real-time.
3. Leverage automation and orchestration
It is no surprise that automation and orchestration platforms are leading the fight against cyber attacks by cutting down human interaction requirements and minimizing human errors.
Open-source tools such as OWASP ZAP allow developers to run specific security assessments on their applications. However, they cannot schedule scans or retain a history of the scans it performs. SOAR tools can.
Security Orchestration, Automation, and Response (SOAR) platforms compile a lot of essential functionalities to make security more efficient and effective. For instance, platforms like Jit enable you to orchestrate and automate various security tools and controls into one platform, making it easier to manage such tools and monitor your application. You can save time without compromising on security.
4. Practice makes perfect
Simulating real-life attacks to test an organization's incident detection processes and readiness is common in all industries. These simulations greatly help organizations test the effectiveness of their security tools and methods, evaluate the skills and knowledge of their incident detection teams, and identify areas for improvement in their processes.
Couple this with cross-training your team to ensure they have a working knowledge of all the security tools and are aware of your security policies. Technology is fantastic, but you need a talented and dedicated team behind it to ensure it works just as you want it to work. Knowledge bottlenecks can be detrimental to increasing your MTTD, which is far from ideal. Ensure that basic security knowledge is spread across the team and your security plan isn’t dependent on just a few engineers or security experts.
5. Log incidents promptly
Having a comprehensive record of incidents enables organizations to understand the context of the attack better and use that information to predict potential failures in the future.
They can access historical data, which helps understand attack patterns and trends, identify areas of weakness in their systems and improve these timely, and respond to incidents faster and more effectively. Logging incidents make it easier for companies to prove compliance with industry standards and regulations such as PCI DSS.
6. Improve troubleshooting and debugging
Minimizing the time wasted during an incident response could save millions of dollars in damage. However, to improve the efficiency of these processes, teams must gather all the debugging and collaboration tools to represent the data within a unified troubleshooting platform. It gives the opportunity teams greater chances of speeding up MTTD and MTTR.
7. Keep learning
Within the cybersecurity landscape, threats constantly evolve, and new attacks and trends are always emerging. Your team needs to stay informed and be prepared for every possible scenario, whether that’s a new type of vulnerability, new tools you can use, or general industry trends.
Lowering your MTTD is easy - trust us.
Measuring your MTTD is vital to understand how well your team is performing. But once you measure it, you need to act on it. Security can be a chore and a complicated one, but including it in your DevOps process is crucial. The more your team understands what they need to do and how they can do it, the easier it will become.
Continuous Security tools are a great helping hand. Add them to proper employee training and a solid and frequently updated security plan, and you have yourself the perfect match.
Jit enables you to orchestrate and automate an extensive range of security tools to protect your entire pipeline and help crush your MTTD. Give us a try and book a demo.