How to Use AWS Secrets Manager in the CLI [With Examples]
That AWS Secrets Manager CLI is a master of secret management—is no secret at all. Learn secret commands that turn whispers into security.
Updated March 5, 2024

Credentials and secrets help protect your systems, but if poorly managed, they can quickly get into the hands of cyber attackers. A hacker with unlimited access to your credentials can cause severe damage.
Secrets are to hackers what candy is for kids—they just can’t seem to get enough of it:
A staggering 37% of cyberattacks result from stolen credentials, so you can’t afford not to manage your secrets properly.
The AWS Secret Manager tool was built with these risks in mind. It helps AWS users secure and store sensitive information run on their clouds, which can then be complemented by tools like Gitleaks, focused on secret detection.
Let's look at how to use the AWS Secrets Manager CLI and explore the service features, along with practical examples in the Command Line Interface.
An Overview of AWS Secrets Manager
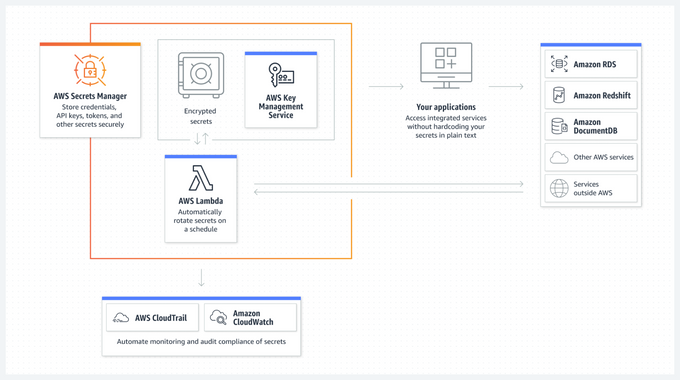
AWS Secrets Manager is a secrets management service provided by Amazon Web Services (AWS). The tool protects sensitive information—access keys, passwords, and API keys—in a secure and centralized way.
With the AWS Manager, you can manage, store, and rotate secrets, so developers and security professionals can follow best practices when dealing with sensitive data in their applications.
Secrets Manager also integrates with other AWS tools and services, such as AWS Identity and Access Management (IAM), AWS Key Management Service (KMS), and AWS CloudTrail.
» Learn how to best use AWS security tools
Understanding Secrets and Their Values
In AWS Secrets Manager, a secret is a logical container for sensitive information consisting of a secret name and one or more secret values.
Secret values are the sensitive data, such as passwords, API keys, or access tokens, that you want to store securely.
Each secret value can have a unique version identifier, allowing you to track and manage different versions of the same secret.
Some examples of secrets include:
- Database credentials, such as usernames and passwords
- API keys for accessing third-party services
- OAuth tokens for authentication and authorization
- SSH keys for accessing servers and other resources
Features of AWS Secrets Manager
1. Securely Store Secrets
AWS Secret Manager lets you securely store secrets in a centralized location and protect sensitive data against unauthorized access and leaks.
All secrets are encrypted using AWS Key Management Service (KMS) keys, which provide additional security and control over your encryption keys.
This secure storage helps you comply with data protection regulations and maintain a strong security posture.
2. Manage the Secret Lifecycle
With AWS Secrets Manager, you can define and manage the entire lifecycle of your secrets—creating, updating, and deleting secrets, along with managing secrets versions and their metadata.
The service allows you to set up custom policies for secret rotation and expiration, and maintain up-to-date and secure credentials throughout your applications.
3. Automate Secret Rotation
One of the key features of AWS Secrets Manager is its ability to automate the rotation of secrets.
The service can automatically generate new secrets and update the ones used by your applications, either regularly or based on custom policies.
Automated secret rotation helps to minimize the risk of compromised credentials and promotes best practices for managing sensitive data.
4. Access Control
AWS Secret Manager integrates with AWS Identity and Access Management (IAM), resulting in finer access control policies for secrets.
You can specify which users or roles have permission to access, modify, or delete secrets so that only authorized personnel can interact with your sensitive data.
This level of control helps you maintain a secure environment and comply with regulatory requirements.
5. Audit and Monitor Secret Usage
Integration with AWS CloudTrail allows you to monitor and audit the use of your secrets in AWS Secrets Manager.
CloudTrail logs all API calls to the service, providing a detailed record of who accessed your secrets, their location, and timings.
You can use this information for security testing, compliance audits, and troubleshooting.
6. Cross-Account Access
AWS Secrets Manager supports cross-account access, so secrets can be shared securely between different AWS accounts.
This feature simplifies the secrets management in multi-account environments. The sensitive data is accessible only to authorized accounts, which further boosts infrastructure security.
Using AWS Secrets Manager in the CLI
You can integrate AWS Secrets Manager through the AWS console, SDK, CLI, or CloudFormation. This section will focus on using the AWS Command Line Interface (CLI).
AWS Secrets Manager CLI is a powerful and flexible tool that allows you to interact with AWS services directly from the command line, automate tasks, and create scripts for various use cases.
Let's look at the examples of how to use AWS Secrets Manager CLI to manage your secrets. These examples convey the basic operations and the syntax for common commands in secrets management.
» CLI is often a key player in best practices for AWS security groups
1. Create a New Secret and Attach Tags
You can use the create-secret command to create a new secret with the AWS CLI.
This command allows you to specify the secret name, value, and optional tags for easier organization and management:
aws secretsmanager create-secret --name MySecret --secret-string "my-secret-value" --tags Key=Environment,Value=Production
The above command creates a new secret named "MySecret" with the value "my-secret-value" and attaches the "Environment" tag with the value "Production."
2. List All Secrets
To list all secrets stored in AWS Secret Manager, use the list-secrets command in CLI:
aws secretsmanager list-secrets
You will then see the complete list of secrets, including their names, ARNs, and other metadata.
3. List All Versions of a Secret
To list all versions of a specific secret, use the list-secret-version-ids command:
aws secretsmanager list-secret-version-ids --secret-id MySecret
4. Get a Secret Value
If you want to get the value of a secret and its additional metadata, such as the version ID and ARN, use the AWS CLI get-secret-value command:
aws secretsmanager get-secret-value --secret-id MySecret
5. Retrieve the Previous Version of a Secret
If you need to retrieve a previous version of a secret, use the get-secret-value command with the --version-id or --version-stage flag:
aws secretsmanager get-secret-value --secret-id MySecret --version-id <previous-version-id>
This command returns the value of the specified previous version of the "MySecret" secret.
6. View the Details of a Secret
To view the details of a secret, including its description, rotation configuration, and tags, use the describe-secret command:
aws secretsmanager describe-secret --secret-id MySecret
7. Modify a Secret
To modify the value of an existing secret, use the update-secret command:
aws secretsmanager update-secret --secret-id MySecret --secret-string "new-secret-value"
8. Create a Secret and Encrypt It With KMS Key ID
To create a secret and encrypt it using a specific AWS KMS key, use the create-secret command with the --kms-key-id flag:
aws secretsmanager create-secret --name MySecret --secret-string "my-secret-value" --kms-key-id <kms-key-id>
9. Create Key/Value Pair Secret from a JSON file
To create a secret with key/value pairs from a JSON file, first create a JSON file with your desired key/value pairs:
{
"key1": "value1",
"key2": "value2",
"key3": "value3"
}
Save the file as my_secret_data.json. Then, use the create-secret command and pass the JSON file as the secret value:
aws secretsmanager create-secret --name MySecret --secret-string file://my_secret_data.json
This command creates a new secret named "MySecret" with the key/value pairs defined in the JSON file.
10. Delete a Secret
To delete a secret, use the delete-secret command:
aws secretsmanager delete-secret --secret-id MySecret
This command deletes the "MySecret" secret. The secret will be scheduled for deletion and removed after the default recovery window of 30 days.
Alternatively, you can use the --force-delete-without-recovery flag to delete the secret immediately without the recovery window.
Enhance Your Secrets Management With Jit
AWS Secrets Manager is a powerful solution for managing your organization's credentials and secrets.
For even more robust protection, Jit orchestrates various open-source security tools such as the AWS security tool Prowler and the secrets detection solution Gitleaks.
Deploying these tools through Jit and scanning only for new code means you can protect your entire CI/CD pipeline much more efficiently.