The 2026 DevOps Guide to AWS Security Tools (+ 4 Best Practices)
AWS security is a constantly expanding hub of simple hosting tools to complex structures. Here's everything you need to know in 2026 to stay up to date with AWS security architecture, tools, and best practices.
Updated September 8, 2025

AI Summary
Amazon Web Services (AWS) has taken over the cloud infrastructure market by storm. Its 34% market share exceeds the combined market share of two of its biggest competitors, Microsoft Azure and Google Cloud. The tech giant offers a full spectrum of tools and cloud services, from simple hosting to complex structures.
As engineering teams deepen their cloud usage and become more agile, they need the right AWS cyber security tools to support modern, complex cloud-native operations. Amazon continues to expand its AWS DevOps portfolio, offering a wide range of tools to help teams increase their agility and speed.
» Make sure you know about the essential steps for web application security testing
Quick AWS Services Overview
AWS, or Amazon Web Services, offers on-demand cloud computing services to individuals, companies, and governments on a pay-as-you-go basis. It is a comprehensive, evolving cloud computing platform that's growing rapidly with new services and features constantly added.
Services include (but are not limited to):
- Computation
- Storage
- Databases
- Analytics
- Networking
- Mobile
- Developer tools
- Management tools
- IoT
- Security
- Enterprise applications
What Is AWS DevOps?
AWS DevOps is a set of tools and services for automating software development and delivery on the AWS platform, enabling you to provision, manage, and deploy AWS resources safely and repeatedly while monitoring and automating your software delivery processes.
AWS DevOps combines two main concepts:
- Infrastructure as code: You can manage and provision your AWS resources using the same tools and processes you use to manage your application code.
- Continuous delivery and integration: You can automatically build, test, and deploy your code to AWS resources multiple times a day.
» Discover the best open-source product security tools
AWS Security Architecture
AWS security is far from simple: it is a multi-layered approach to security that includes tools and technologies for each stage of the software development lifecycle (SDLC).
Security policies and postures are the guidelines and rules that organizations must adhere to protect their data and systems. AWS services can be utilized as tools to implement security measures, such as OWASP ZAP and Gitleaks.
For example, in the early phases of SDLC, AWS identity and access management (IAM) can control access to AWS resources. IAM can also create and manage user accounts and permissions, as well as generate and rotate access keys. You can use AWS Config to audit and monitor resource configurations for compliance.
AWS Security is a constantly evolving service that is always adding new features and tools. For instance, a recently launched AWS Security Hub provides a centralized view of security alerts and findings from multiple AWS services.
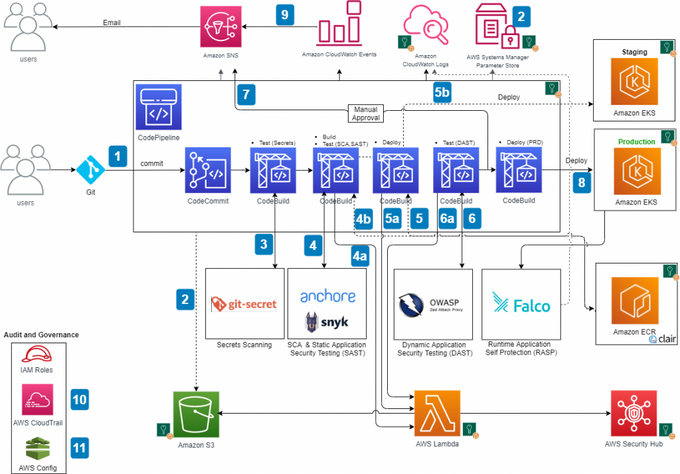
Here is an example of the Kubernetes DeveSecOps pipeline using AWS CodePipeline that includes industry-grade security tools integration. Git secrets scanning presents itself as the first test for the security pipeline, followed by SAST, DAST, and RASP tools.
» Confused? Learn the difference between SAST and DAST
AWS CodePipeline is a continuous delivery service that helps you automate your software release process. Third-party security integrations within the code pipeline allow teams to offload the task of secret scanning and automate continuous security protocols.
Security-first platforms like JIT can help integrate SAST tools, DAST tools like OWASP ZAP, and secret scanning like Gitleaks.
AWS Security Categories
- Identity and access management: This category of tools helps you manage users and their permissions to access AWS resources. Examples include IAM, Cognito, and STS.
- Detection: This service helps you detect potential security threats and breaches. Examples include Inspector, GuardDuty, and Macie, all well-regarded solutions that can help detect potential security threats and breaches.
- Prevention: These tools help you prevent unauthorized access to your AWS resources. Examples include WAF, Shield, and VPC.
- Auditing and monitoring: These tools help you detect and keep track of suspicious activity in your AWS environment. Examples include CloudTrail, CloudWatch, and Config.
4 Best Practices for AWS DevOps Security
Aside from the standard best practices and techniques of AWS DevSecOps professionals, such as using IAM roles for least privilege, using security groups and network access control lists, and encrypting data at rest and in transit, there are a few other things you can do to ensure that you maintain control over your system and security.
1. Adopt Continuous Integration/Continuous Delivery
CI/CD security helps developers avoid merge conflicts, ensures that the codebase is always in a deployable state, and makes it easier to roll back changes if necessary. It also enables development teams to release new features and fixes more efficiently.
Continuous integration (CI) is a software development practice in which developers regularly merge their code changes into a shared code repository.
Continuous delivery (CD) is a software development practice in which code changes are automatically built, tested, and deployed to production.
2. Automate Infrastructure
Automating infrastructure can improve code quality by reducing the need for manual input and increasing the accuracy of deployments. By automating infrastructure, you can free up time for developers to focus on other tasks and help avoid errors that can occur when manually configuring infrastructure.
3. Continuously Monitor and Log Your Software
Continuously monitoring and logging your software is essential because it allows you to identify issues in real-time and fix them before they cause significant problems. Additionally, logging provides a record of what your software was doing at any given time, which can be helpful for debugging purposes.
4. Utilize AWS DevOps Security Tools
Continuous monitoring, logging, and auditing are crucial to maintaining the safety of applications. By keeping track of activity and knowing what has happened in the past, it is possible to identify and fix problems that may arise more easily.
Here are some cloud security tools in the AWS DevOps security hub that you should consider integrating into your cloud operations to make the job easier:
- Amazon CloudWatch: Security monitoring service for AWS cloud resources and the applications you run on AWS that grants system-wide visibility into resource utilization, application performance, and operational health. You can use CloudWatch to collect and track metrics, collect and monitor log files, set alarms, and automatically react to changes in your AWS resources.
- AWS CloudTrail: An AWS vulnerability scanning tool that enables governance, compliance, operational auditing, and risk auditing of your AWS account. With CloudTrail, you can log, continuously monitor and retain events related to API calls across your AWS infrastructure, and the service provides the event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services.
- AWS Identity and Access Management: This service helps you securely control access to your AWS resources. IAM lets you create and centrally manage users, security credentials such as passwords, keys, and access policies that control which users and resources can access your AWS account.
- AWS Config: Service that enables you to assess, audit, and evaluate the configurations of your AWS resources. AWS Config lets you review changes to your resources and maintain an inventory of all your AWS resources.
What It Takes to Supercharge Your DevOps Security
Many tools are available to help you harden your security posture. However, tools by themselves don't do much unless they are implemented. Jit sits within an AWS environment and works as an orchestration layer that enables developers to easily integrate security tools such as AWS 2FA, AWS runtime misconfig, AWS Least Privilege IAM, and many others.