Navigating DevOps Compliance Solutions: Key Considerations
Updated February 28, 2024.

The role of DevOps was initially envisaged to bridge the gap between the software supply chain's development, release, and operational processes. But over the years, it has taken a pivotal role in unifying all aspects of software delivery, including security.
Rising cybersecurity threats are keeping governments and regulatory agencies on their toes. With newer frameworks introduced every few years and current regulations becoming stricter, businesses must be on their A compliance game. And they know it’s not about working harder but smarter. For example, the use of spreadsheets to manage IT compliance decreased from 43% in 2022 to only 10% in 2023.
DevOps is a viable option to simplify compliance management. With over a decade-long refinement cycle, DevOps practices have now attained a level of maturity wherein they can incorporate additional processes for something as vital as security - alleviating some of the burden regulatory compliance poses on already overloaded IT teams.
Why do you need DevOps compliance solutions?
The growing complexity of regulations and the rising sophistication of cyber threats place organizations under intensified scrutiny to ensure data protection. From the European Union’s GDPR, intended to safeguard personal data, to HIPAA, focused on the healthcare sector, all businesses have an overwhelming list of varying requirements they must comply with.
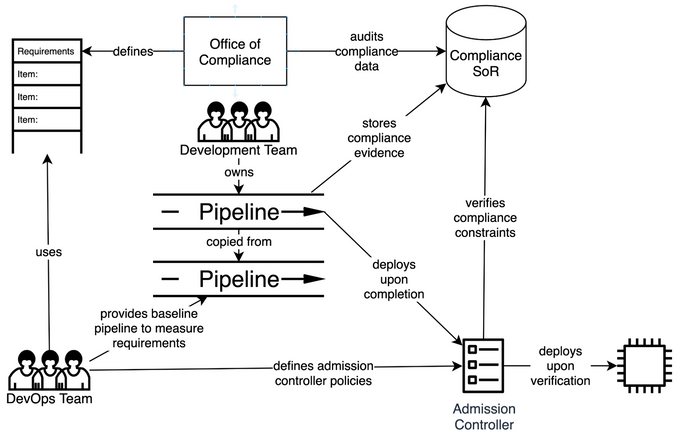
With the increasing influence of DevOps on the control and oversight of the pipeline, it became evident that we could customize the pipeline stages to include additional processes. Thus, a new opportunity arrived in the way of a DevOps compliance solution, leveraging DevOps to shift security left.
A DevOps compliance solution incorporates additional security rules and regulatory checks in the pipeline. For example, suppose a developer commits code that can cause a data breach or unauthorized system exposure. In that case, the pipeline's CI process will scan the code against the rules and flag the issues back to the developer. In this way, many infosec and cybersecurity-related regulations can be embedded within DevOps to ensure that all security concerns are addressed in the software integration and delivery phases.
It is also a logical step to upgrade the DevOps practice since DevOps has complete visibility of all the deployment infrastructure. Therefore, it has the potential to foster better collaboration between the Dev and Ops teams with the security teams, who would otherwise have worked in silos trying to mitigate security incidents in the infrastructure.
7 key considerations of DevOps compliance solutions
1. Automation
Automation is the catalyst for propelling every DevOps pipeline. Apart from enabling improved efficiency and faster releases, automation establishes a closed-loop system to monitor issues and mediate any exceptions in the pipeline with minimum human intervention.
Implementing a security compliance solution requires several additional measures in the overall automation capabilities. These include monitoring the source code modifications, scanning them for security issues such as malicious code, detecting nonconformance during testing, and performing auto-remediation for known vulnerabilities.
Another important consideration is the security gates. Automation enables closed-loop feedback to evaluate a deployed application against compliance policies. With end-to-end provisioning of this capability across all pipeline stages, you can achieve continuous compliance, which is the ultimate goal of any DevOps compliance strategy.
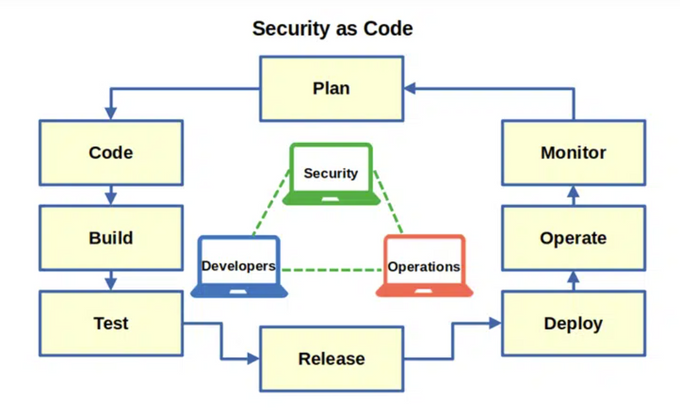
2. Security as Code
Traditionally, compliance checks were enforced as a manual process under a separate department that would handle all the legal conformance, including infosec and cyber security regulations. The manual process is fraught with human error, and for a large enterprise, enforcing compliance takes many person-hours of additional effort over and above the software release timelines.
Codified compliance ensures that all the compliance checklists are baked into the DevOps pipeline as an objective set of rules. It relies on a declarative syntax around the Security as Code (SaC) approach, so all security checks, tests, and gating criteria can be incorporated within the pipeline without repeated manual effort.
Jit can codify all your compliance requirements thanks to its extensive support for code-level security tools. You can orchestrate and manage these tools from a single interface, simplifying SSDLC security. It also supports cloud infrastructure-related security compliances like Prowler for AWS. Prowler is a powerful open-source security tool with over 200 controls covering various security frameworks such as PCI DSS, AWS FTR, ISO27001, GDPR, HIPAA, FFIEC, SOC2, and ENS.
3. Enriched reporting
All DevOps solutions have a system of record for capturing events, status, errors, and warning messages about the pipeline operations, with timestamps and user identifiers. This system is a single source of truth for DevOps security compliance. It documents all activities on the pipeline and captures traces of security incidents and the audit trail of all users.
From a conformance standpoint, it also enables one-click compliance verification, such that the DevOps administrators or release managers can ascertain the level of compliance achieved at each pipeline stage with remediation suggestions.
Jit centralizes the visibility into pull requests with at-a-glance identification of ongoing issues in PRs, compliance verification reports, and security backlogs. It provides enriched reports by compiling findings from various security tools and offers real-time remediation so teams can mitigate known vulnerabilities quickly and efficiently.
4. Cross-functional collaboration
DevOps platforms offer various options for cross-functional team collaboration, from messaging and email notifications to collaborative code reviews. While all these collaboration options are equally applicable to DevOps compliance solutions, the overall DevOps workflow gets more intricate due to the assimilation of security processes.
A DevOps compliance solution must break down the collaboration barriers to address these complexities. One example is sharing vulnerability information and performing remediations through cross-functional interaction during code reviews or incident response handling. The solution should also provide a cross-functional knowledge base to enhance the understanding of security and compliance across development and operations teams.
5. Integrations
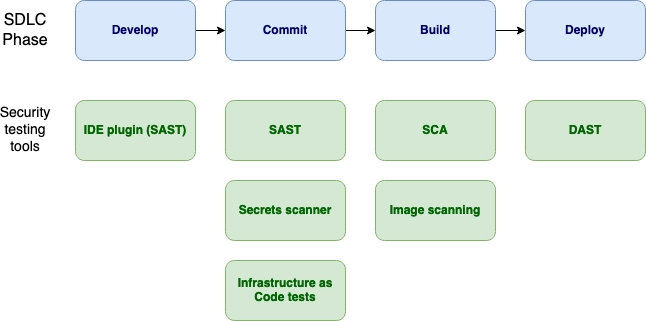
On top of the base version control system that manages the pipeline, DevOps platforms must also support a host of third-party integrations. The additional integrations should include:
Static code analysis: Identifies security vulnerabilities in the source code during development via SAST tools.
Dynamic testing: Tests applications and detects runtime vulnerabilities via DAST tools.
Vulnerability management: Used to manage an internal directory of known vulnerabilities and interfaces with third-party vulnerability and threat intelligence feeds.
Secrets management: Helps to prevent secrets sprawl by securely managing, storing, and distributing sensitive information such as private keys, passphrases, and certificates.
Incident management: Used to collect and analyze security data, easing incident response.
6. Industry Frameworks
Industry frameworks cover security, governance, and risk management for specific industries. These frameworks provide a structured approach to managing safety within a DevOps practice, so your solution must cover every regulation and framework that affects you. Some of the most critical frameworks include:
PCI DSS: Safeguards cardholder information.
GDPR Governs the capture and sharing of personal data within the European Union.
HIPAA: Protects the confidentiality of health information.
NIST: Enables security and privacy controls to mitigate information security risks.
An ideal way to incorporate these DevOps standards is through templatized SaC artifacts containing rules for each framework.
7. Customization
Finally, you must consider capacity, customization, and cost factors. This requires configuring the compliance solution to support a certain number of parallel pipelines, environments, users, and activities as per the scale of the day-to-day DevOps processes.
This process ties back to all the previous considerations to ensure an efficient pipeline administration without causing additional delays or burdens on the teams. Most importantly, it should be cost-effective for the scale at which the organization plans to manage its DevOps practice. Yet, it must be flexible enough to incorporate newer security processes and third-party integrations with minimal downtime.
Striking a balance between agility and compliance in DevOps
DevOps has long ensured an agile and high-velocity software delivery pipeline. But now, the new-ish kid on the block, DevSecOps, is taking the DevOps game to a new level. The much-needed intersection of development, operations, and security helps companies maintain the same velocity of software release cycles without grappling with an ever-evolving regulatory landscape.
Choosing a feature-rich DevOps compliance solution is crucial to embedding security swiftly into your pipelines and ensuring continuous compliance. Jit’s DevSecOps orchestration platform supports a host of tools that can be incorporated into your code, environment, and underlying version control system to give you end-to-end, ironclad security. Explore Jit to learn more.